Are you a member of the Splunk Community?
- Find Answers
- :
- Premium Solutions
- :
- Splunk Enterprise Security
- :
- How do I use regex to select a string between two ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
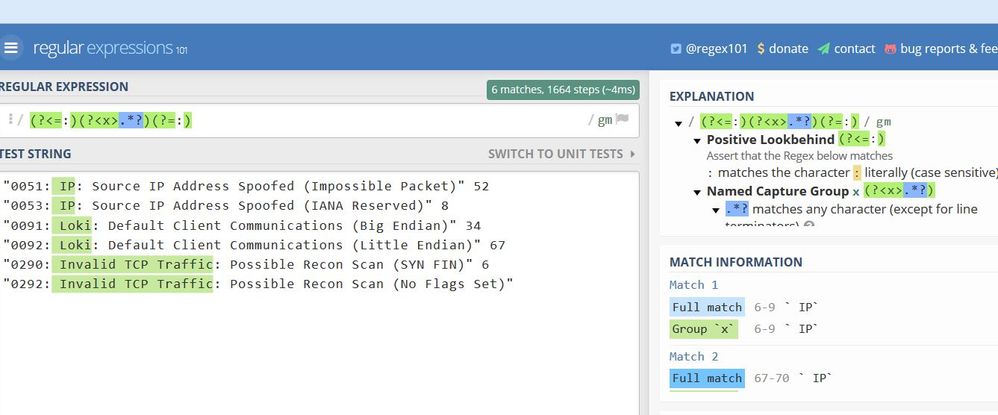
I have a field (myfield) whose values are as follows:
"0051: IP: Source IP Address Spoofed (Impossible Packet)" 52
"0053: IP: Source IP Address Spoofed (IANA Reserved)" 8
"0091: Loki: Default Client Communications (Big Endian)" 34
"0092: Loki: Default Client Communications (Little Endian)" 67
"0290: Invalid TCP Traffic: Possible Recon Scan (SYN FIN)" 6
"0292: Invalid TCP Traffic: Possible Recon Scan (No Flags Set)"
I would like to select the text between the colons (i.e. IP, Loki, etc) and create a new field from that text. My search is:
my search | rex field=myfield "(?<=:).*?(?=:)"
This returns the following error:
Error in 'rex' command: The regex '(?<=:).*?(?=:)' does not extract anything. It should specify at least one named group. Format: (?...).
This works in my regex testing. Any help would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
One of my favorite regexes (and I see Splunk use this in their config sometimes which is where I learned it) is a character class that is not the value of the ending capture like so:
| rex field=myfield ":\s+(?<newfield>[^:]+):"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
thanks everyone. new to regex 🙂
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please accept the answer that helped you .
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
One of my favorite regexes (and I see Splunk use this in their config sometimes which is where I learned it) is a character class that is not the value of the ending capture like so:
| rex field=myfield ":\s+(?<newfield>[^:]+):"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Try this, you should get the desired value in text field
| rex field=myfield ":\s+(?<text>\S+):"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content