- Apps and Add-ons
- :
- All Apps and Add-ons
- :
- Re: How to parse "WinEventLog:Windows PowerShell"?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to parse "WinEventLog:Windows PowerShell"?
My question is how have others been parsing this Powershell file among other esoteric Windows Event logs? Currently I am using the Splunk app TA_windows. It parses some of the generic logs quite well. Will effort be done by Splunk or the community to parse other such logs? Am I going about this completely wrong?
Here is my immediate regex issue. I want to extract the field HostApplication. As you can see the line may be one or two lines in the raw event.
This works in the search bar but does not work as an extracted field.
| rex field=_raw "HostApplication=(?P.+\s(?=\s))"
Field extraction = HostApplication=(?P.+\s(?=\s))
_raw event=
LogName=Windows PowerShell
SourceName=PowerShell
EventCode=400
EventType=4
Type=Information
ComputerName=ABC-123
Keywords=Classic
Message=Engine state is changed from None to Available.
Details:
NewEngineState=Available
PreviousEngineState=None
SequenceNumber=13
HostName=ConsoleHost
HostVersion=5.1.14409.1005
HostId=9b3e7caa-29af-42fe-8cfe-b6d6c9d83ead
HostApplication=C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe -NoLogo -Noninteractive -ExecutionPolicy Bypass & 'C:\WINDOWS\CCM\SystemTemp\4eef3f2ec987c2.ps1'
EngineVersion=5.1.14409.1005
RunspaceId=33010d86-d566-434f-aa74-ebb0b0b600fa
Can someone help with the strategic questions and my immediate regex issue?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am joining the question as the extractions seems not to be prebuilt in the Windows TA
here is how i worked around it:
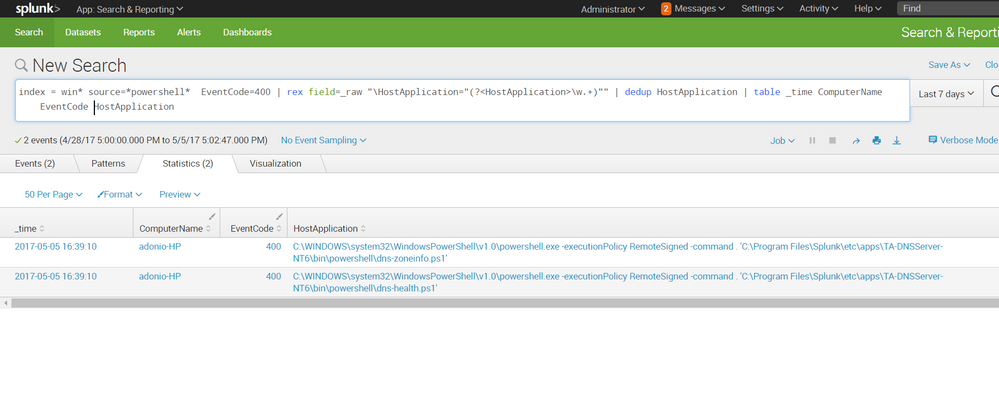
index = win* source=*powershell* EventCode=400
| rex field=_raw "\HostApplication="(?<HostApplication>\w.+)""
| dedup HostApplication
| table _time EventCode ComputerName HostApplication
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
is there any way we can extract all the fields present in message field automatically ?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I also need to know this.
I'm struggling to extract the 'CommandLine' field as everything below the 'RunspaceId' is missing when I try to extract new fields.
I'm looking at event ID's 500 & 501 and using the app Splunk_TA_windows.
UPDATE
I think I've managed it by using the following in-line regex...
| rex field="Message" ".CommandLine=(?.$)"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It is the Splunk add on for Windows (Splunk_TA_windows)
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
can you share the input you are using in inputs.conf to get these events?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
[WinEventLog://Windows PowerShell]
disabled = 0
whitelist=800,400
index = wineventlog
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@kinkster - Which Splunk app/add-on are you using from Splunkbase: Splunk Add-on for Microsoft Powershell, Splunk Add-on for Microsoft Windows, or something else? I just want to make sure your post is tagged appropriately.