Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- stats latest not showing any value for field
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
stats latest not showing any value for field
Hi,
We have following query -
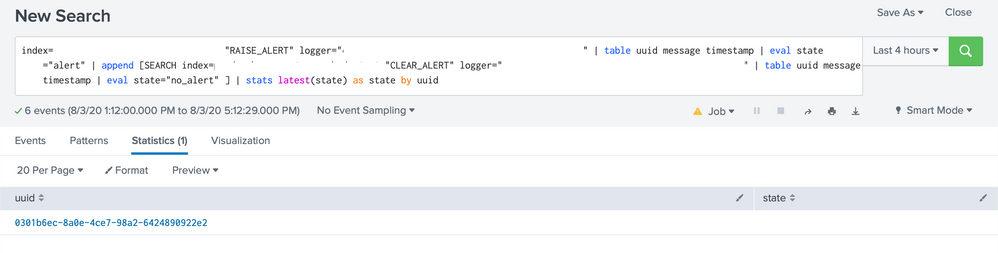
index=yyy sourcetype=zzz "RAISE_ALERT" logger="aaa" | table uuid message timestamp | eval state="alert" | append [SEARCH index=yyy sourcetype=zzz "CLEAR_ALERT" logger="aaa" | table uuid message timestamp | eval state="no_alert" ] | stats latest(state) as state by uuid
But this query is not showing anything for state, it shows only uuid.
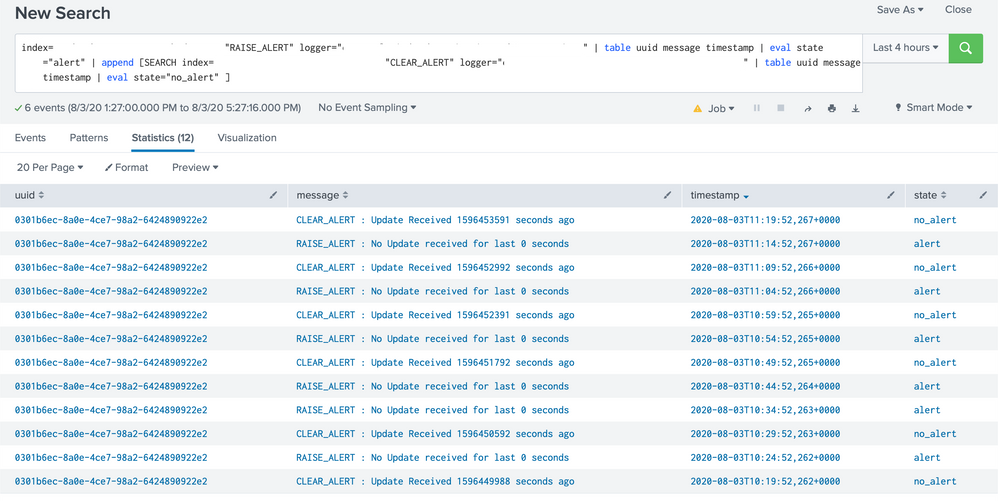
Query before and without latest works just fine. Here is screenshot of result of everything before stats -
If we replace stats latest with stats last, we can see uuid and state, its just not the last observed value of state for that uuid.
Any idea as to why this can happen?
Update :
Figured out the issue with this - the fields are being extracted using table, but there is no way for query to figure out the timestamp using extracted fields. Fields extraction is not needed for our use case anyway, removing both table clauses makes the query work.
This is the updated query, this works -
index=yyy sourcetype=zzz "RAISE_ALERT" logger="aaa" | eval state="alert" | append [SEARCH index=yyy sourcetype=zzz "CLEAR_ALERT" logger="aaa" | eval state="no_alert" ] | stats latest(state) as state by uuid
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There are a few things you can try. The first is to include _time in the events.
index=yyy sourcetype=zzz "RAISE_ALERT" logger="aaa" | fields _time uuid message timestamp | eval state="alert" | append [SEARCH index=yyy sourcetype=zzz "CLEAR_ALERT" logger="aaa" | fields _time uuid message timestamp | eval state="no_alert" ] | stats latest(state) as state by uuidThe second is to use dedup in place of stats.
index=yyy sourcetype=zzz "RAISE_ALERT" logger="aaa" | fields uuid message timestamp | eval state="alert" | append [SEARCH index=yyy sourcetype=zzz "CLEAR_ALERT" logger="aaa" | fields uuid message timestamp | eval state="no_alert" ] | dedup state uuidFinally, this search should be faster since it only scans the index once.
index=yyy sourcetype=zzz ("RAISE_ALERT" OR "CLEAR_ALERT") logger="aaa"
| eval state = if(searchmatch("RAISE_ALERT"), "alert", "no_alert")
| fields _time uuid message timestamp
| stats latest(state) as state by uuidIf this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the solutions.
Tried second and third solution.
Second solution seems to be showing entire raw logs, not extracted fields.
Third Solution is showing only uuids that have state as alert.
Figured out the issue with the original query, updating description.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If this reply helps you, Karma would be appreciated.