Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How to substract values from two different fields ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi all.
I have a FIELDX with values like:
VALUE1 200
VALUE2 120
VALUE3 156
Also, I have another field FIELDY, values:
VALUE1 120
VALUE2 76
VALUE3 54
I want to show in a table a new field showing the difference between FIELDX and FIELDY per VALUE. I mean:
FIELDZ
VALUE1 80
VALUE2 44
VALUE3 102
I tried with a simple ... | eval FIELDZ=FIELDX-FIELDY, but that didn't work.
How I can do this?
Thanks!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
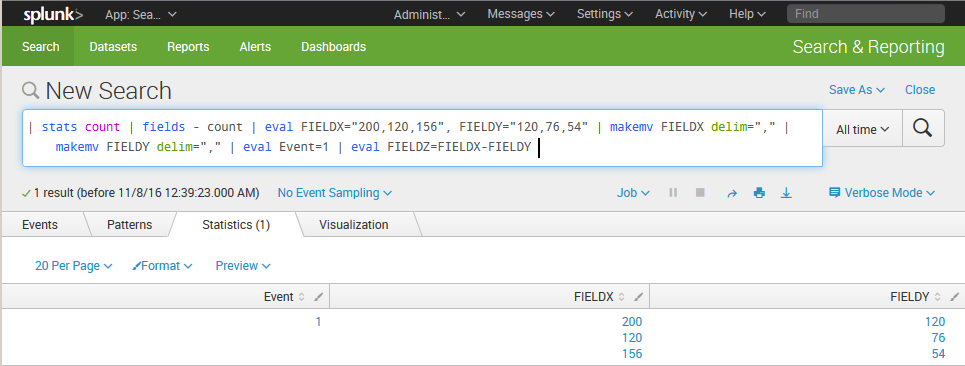
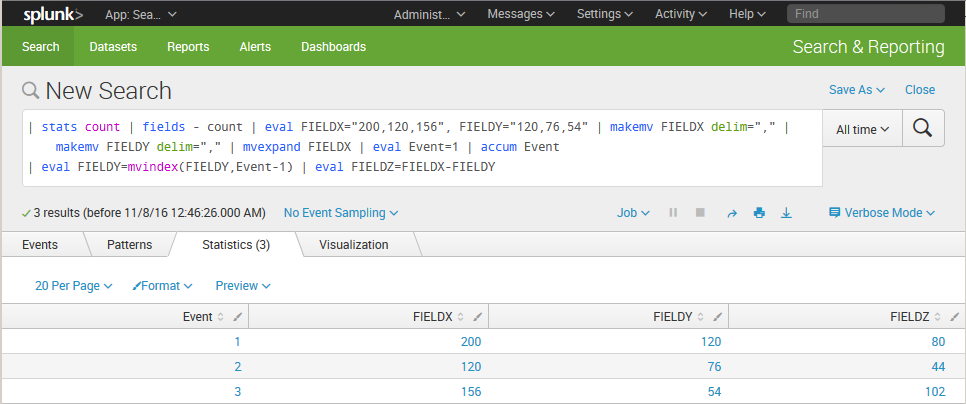
Is it possible that there is a single event which contain two fields, each with multiple values? In this scenario, the fields are the equivalent of arrays which hold a list of values and lists cannot be added together. Simply put: the operation needs to use a single value against a single value at a time.
Do you notice the eval statement at the end of the search?
If this were the case, it will be necessary to break down the multi-value fields using some transformation commands. For the example above, the following works.
As other Splunkers point out above, it will be important to understand how the data is being presented. From there, the transformation can happen in number of ways. This is just an example based on intuituion... but it may not reflect your reality.
I hope this helps,
-gc
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is it possible that there is a single event which contain two fields, each with multiple values? In this scenario, the fields are the equivalent of arrays which hold a list of values and lists cannot be added together. Simply put: the operation needs to use a single value against a single value at a time.
Do you notice the eval statement at the end of the search?
If this were the case, it will be necessary to break down the multi-value fields using some transformation commands. For the example above, the following works.
As other Splunkers point out above, it will be important to understand how the data is being presented. From there, the transformation can happen in number of ways. This is just an example based on intuituion... but it may not reflect your reality.
I hope this helps,
-gc
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ive never done it, but you may try
|eval fieldx=(fieldX - fieldy)
I know you tried something similar, but I recall that functions usually need to be enclosed to work.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What is the format of the event? JSON? Posting the event might be helpful!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ideally based on the example the above should work. Have you tried printing table FIELDX FIELDY FIELDZ? Are the two fields FIELDX & FIELDY numeric?
Please provide Splunk search query and sample FIELDX and FIELDY.
| makeresults | eval message= "Happy Splunking!!!"