Join the Conversation
- Find Answers
- :
- Splunk Platform
- :
- Splunk Enterprise
- :
- Re: how can i timechart with a _time multivalue ?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi all,
I want to timechart the ouput of my stat command. I know that the _time field must be in the stats command when i add _time in the stats command, _time appears like a multivalue field so how can i timechart with this field ?
index="X" sourcetype="Y" | stats values(A) AS NOM values(eval(round(B/60))) AS duration distinct_count(C) as cparticipant values(_time) as time by call_id | where duration >=2 and cparticipant>1 | join NOM [| inputlookup D]
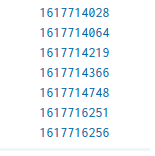
here the field _time
Thx
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
timechart expects the _time field to be single-valued. Similarly, the stats functions timechart supports all expect a single-value argument.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
timechart expects the _time field to be single-valued. Similarly, the stats functions timechart supports all expect a single-value argument.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Rather than values(_time), try min(_time) or max(_time) to use the oldest or newest timestamp, respectively.
That may be only the first of your problems as I suspect timechart will have difficulty displaying multi-value fields.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I used the eventstats command and it works! But the command takes a long time to execute whereas with stats it is done almost immediately.
so its possible to timechart with mv field _time ?
