- Splunk Answers
- :
- Splunk Premium Solutions
- :
- Security Premium Solutions
- :
- Splunk Enterprise Security
- :
- Re: How to Create Conditional Alerting based on Lo...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to Create Conditional Alerting based on Lookup Tables
I currently have alerting setup for authentications that occur from outside of the country. However, I would like to suppress alerting for specific users for x amount of time.
For example an alert for John Smith logging from Australia. Once I validate that this in fact John Smith, I want to write this entry to a lookup table and suppress any future alerts from him for lets a say 1 week to avoid alarm fatigue. Below is what I have so far. Not sure where to go from here or if i'm even headed the right direction with this.
index="authenticatior" action=success | search "location.country"!="" AND "location.country"!="US" | table _time device,username,user_first,user_last,user_managedBy,factor,integration,result,location.city,location.country
|eval _time=strftime(_time, "%m/%d/%y %I:%M:%S:%p")
| rename _time as Timestamp location.city as City, location.country as Country user_managedBy as Manager username as "User ID" user_first as First, user_last as Last, factor as Factor integration as Integration result as Result device as Device
| sort Last
| inputlookup append=t mylookup.csv
| outputlookup mylookup.csv
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have tried both suggestions at this time. Rewrote the alert and kept the original username field as is. However, all alerts are being suppressed as opposed to repeat user logins. Thinking the lookup table might be the more viable option here,
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
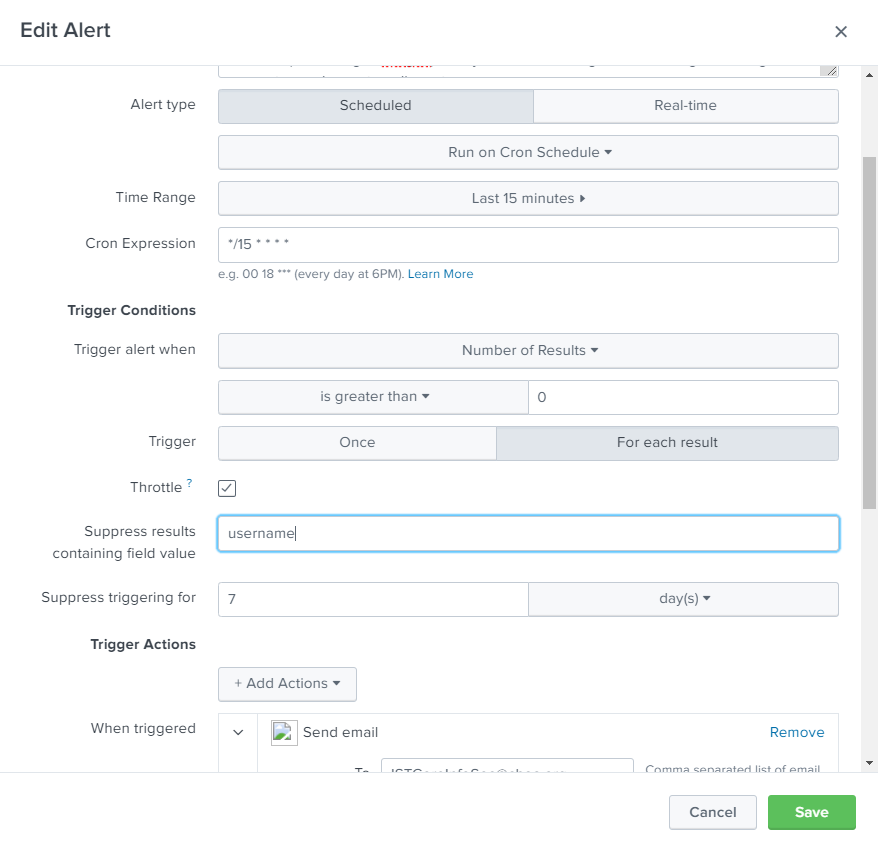
I see you are renaming the field "username" to "User ID" in your search above.
So you should enter "User ID" in the field "Supress results containing field value".
(However, I'm not sure if spaces are accepted or if you have to use double quotes.)
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I did try the User ID field initially, but not with the double quotes. I will try this and provide feedback.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If it doesn't work, then don't rename "username", or rename username to User_ID (without spaces).
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
whrg,
I will give this a try and validate over the next few days. Thanks
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Instead of using a lookup table, how about using the throttle feature for alerts? You could throttle your alert based on the username.