Are you a member of the Splunk Community?
- Find Answers
- :
- Splunk Administration
- :
- Getting Data In
- :
- Re: how to create a table to show port status of C...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
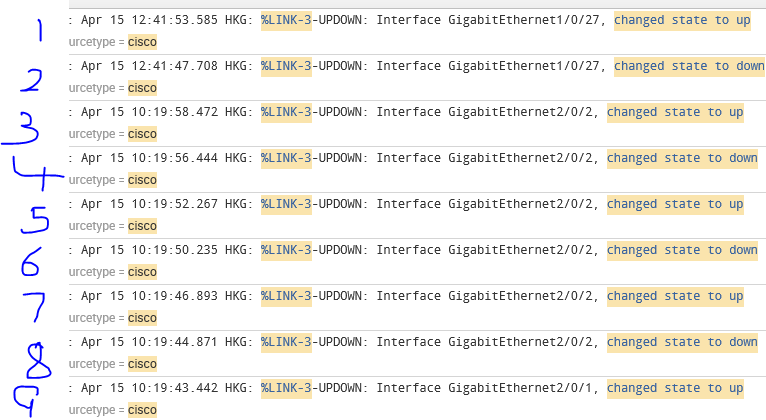
Cisco has been configured and sent syslog to Splunk as follows:
I would like a table to show port status of Cisco switch with format as follows:
Interface status count
GigabitEthernet1/0/27 up 1
GigabitEthernet1/0/27 down 1
GigabitEthernet2/0/2 up 3
GigabitEthernet2/0/2 down 3
GigabitEthernet2/0/1 up 1
GigabitEthernet2/0/1 down 0
Can someone help to complete the search below (or come with some regex) to achieve this? great thanks!
(sourcetype=cisco ("%LINK-3") AND ("changed state to up" OR "changed state to administratively up")) OR (sourcetype=cisco ("%LINK-3") AND ("changed state to down" OR "changed state to administratively down")) | table Interface, status, count ???
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Install and configure the Cisco Networks Add-on and Cisco Networks App, both available from Splunkbase. You will get all the extractions and the overview page has the search you need in a panel called Port Flapping.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Install and configure the Cisco Networks Add-on and Cisco Networks App, both available from Splunkbase. You will get all the extractions and the overview page has the search you need in a panel called Port Flapping.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks, in fact i did install both Cisco Networks Add-on and Cisco Networks App.
But there seems no outputs at all. Please see their configurations below:
https://imgur.com/ftwtoZj
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Your sourcetype is cisco whereas the add-on requires it to be cisco:ios
See if changing it helps.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
thx again. in fact I did change it already. In the screenshot I attached, I have changed it as follows:
Name: Search string:
cisco_ios sourcetype=cisco
but it somehow does not work at all
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You need to set the sourcetype to cisco:ios upon ingesting the data in Splunk. Do it on the input you defined.
Notice that it is cisco colon ios
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
thx mikaelbje, it does work now.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey @splunkbeginner if your logs are always in the same format you can extract the field using rex
your search |rex field=_raw "Interface (?<Interface>[A-Za-z0-9_/.-]*)" | rex field=_raw "to (?<status>\w+)" | stats count by Interface,status
Hope this will help!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
thanks riddhichandarana, it certainly helps!