Are you a member of the Splunk Community?
- Find Answers
- :
- Splunk Administration
- :
- Getting Data In
- :
- Re: How to merge lines based on timestamps?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to merge lines based on timestamps?
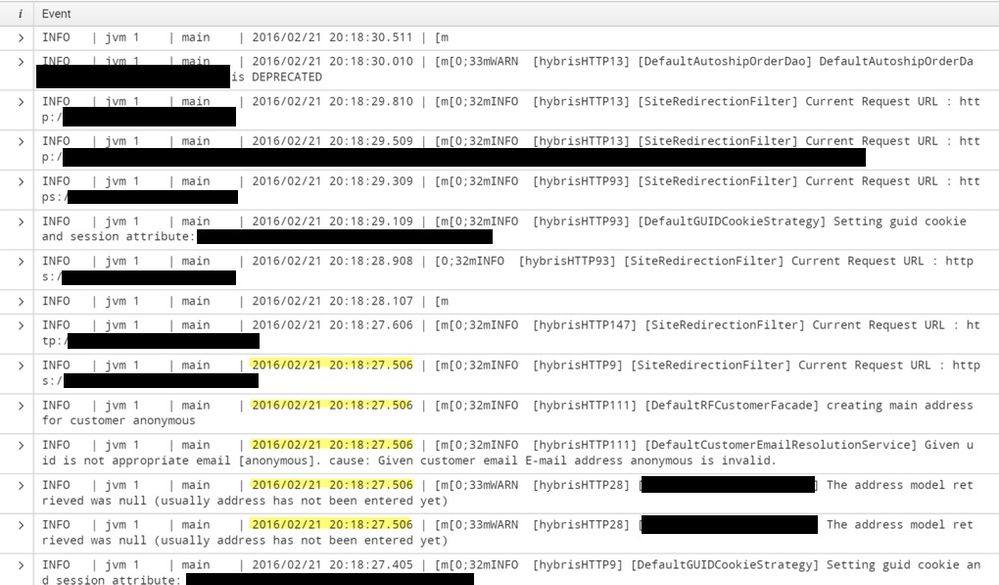
Attached is a screenshot of the way my logs are appearing in Splunk. They match the log files themselves exactly, separating out each entry regardless of the timestamp. The pattern is the same for each new event (INFO | JVM1...) and we want to try to “linemerge” events that have the same exact timestamps (Examples hightlighted).
How would I approach this issue?
Thanks!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
At search time, try the transaction command.
Or use the poor man transaction " ... | stats values(_raw) by source sourcetype host index _time "
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Do you want to merge them at index time or search time?
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@richgalloway How to do it during index time? What changes need to be made in line break settings?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You may be able to adjust the props.conf settings to change how events are ingested. Can you share raw events?
If this reply helps you, Karma would be appreciated.