Are you a member of the Splunk Community?
- Find Answers
- :
- Splunk Administration
- :
- Deployment Architecture
- :
- Re: Time Bucket Displayed
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Time Bucket Displayed
Hi,
is there anyway I can display what time bucket has been applied when displaying single values? My users would like to know to what time span the count in a single value applies to ...
Thank you,
Rob
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I think that what you are asking is "When I do not manually specify a span= argument to timechart, is there a way to programatically see what timechart used?" If so, then the answer is "Yes!" It creates an invisible (because it begins with an underscore character) field called _span (units are seconds) which you can easily access programatically with an eval based token.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is exactly what I am looking for, however, I do get the following error:
Warning on line 87: Invalid child="eval" is not allowed in node="single"
I cannot add the eval token to the base search as there is no timechart in it.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Obviously, you cannot reference something that does not exist yet. Download the `Splunk 6.X Dashboard Examples" app and see how this kind of thing is done:
https://splunkbase.splunk.com/app/1603/
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
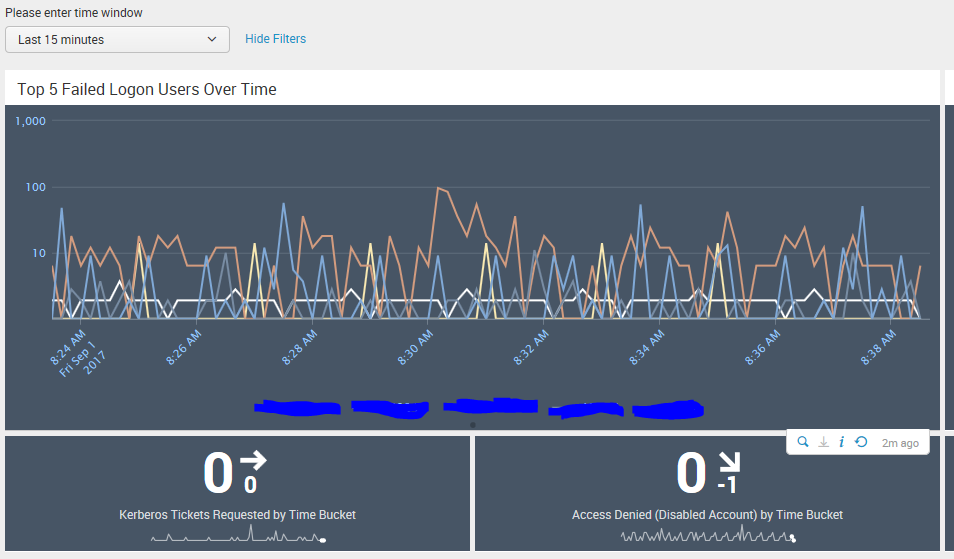
What I am looking for is the span of each time bucket...
Let me all a screenshot...
For the single value panels at the bottom of the dashboard I would like to reference the period of time the latest count covers, in a duration type of metric. For example, the trendline is a great way of checking patterns but the single value 30, for example, doesnt necessarily tell me what period this covers compared to the previous value.
I believe what we probably need is a token set with the time bucket span used by the search head...
THank you, guys!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I guess I don't understand what a "time bucket" is in this context. In a comment to another answer you mention, " I am looking for the duration of each bucket span, no the span of the entire search" - what does that mean? What is "each bucket span" - I can't tell if you're referring to an actual Splunk bucket or just using the term generically to mean a span of time.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
sure .... I am not talking about Splunk's hot, warm, cold data buckets, etc, but when we "bucket" time, such as:
index=_internal| bucket _time | stats count by _time
I am fully aware that you can manually set the time span ( |bucket _time span=15min| , for example) but I would like Splunk to determine the best range. Does this make any sense?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I thought you might be timecharting (or bin/stats) the data, but wanted to be sure. I'm not sure there is a way to get what you're asking since the binning is done dynamically and internal to those functions.
I'm not sure why it matters since the count by _time is still over the min(_time)/max(_time) of all events regardless of how it's binned. So your single value time span is still that. Unless you're trying to match time spans to the sparkline in the single value. At that point, you might as well just add a drilldown to the single value to show the timechart.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
To be honest, I just want the dashboard users to know what time span was used in a single value panel...
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
then max(_time) - min(_time) should do it, but you'd want to do that before Splunk bins _time or you'll lose some granularity. Look at my answer above with an example single value to see how to set the tokens and such - should get you started.
You'll have to parse the span to how you want it displayed since the value will be a span of seconds, but Splunk does have tostring(val, "duration") if you want a quick way. I'm not fond of the format, but it's built in.
I use this for span formatting
replace(replace(tostring($field$, "duration"), "^(?:(?:(?:(\d+)\+)?0?(\d{1,2}):)?0?(\d{1,2}):)?0?(\d{1,2})", "\1d \2h \3m \4s"), "((?<!\d)0?[dhm]\s)", "")
just replace $field$ with a value representing seconds
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The answer is yes, but I'm not sure which "time bucket" you're asking about. There is the time span the user chose to display (like from a time picker) and then there's the event data set time span (earliest event's _time to latest event's _time).
I'll give an example that uses both
<dashboard>
<label>Test Dashboard</label>
<search id="singleBase">
<query>
index=_internal sourcetype=splunkd component=Metrics group=queue name=indexqueue
|addinfo
|stats min(_time) as et, max(_time) as lt, last(info_min_time) as info_min_time, last(info_max_time) as info_max_time, count
|convert ctime(info_max_time), ctime(info_min_time), ctime(et), ctime(lt)
</query>
<earliest>-5m@m</earliest>
<latest>now</latest>
<finalized>
<set token="EVENT_SPAN">$result.et$ to $result.lt$</set>
<set token="SEARCH_SPAN">$result.info_min_time$ to $result.info_max_time$</set>
</finalized>
</search>
<row>
<panel>
<title>Data from $SEARCH_SPAN$</title>
<single>
<search base="singleBase">
<query>|fields count</query>
</search>
<option name="drilldown">none</option>
<option name="underLabel">$EVENT_SPAN$</option>
</single>
</panel>
</row>
</dashboard>
The event set span is min(_time)/max(_time) and the search span is retrieved via addinfo's info_min_time/info_max_time.
The base search is used to set up the tokens. The single panel uses a post process search to get its value. The tokens are used by the single panel in the title and as the caption option just to show how they could be used.
This single panel options are for 6.6.2 - not sure when they changed since I went from 6.3.4 to 6.6.2 and in 6.3.4 the option names are different. But this shows the general idea regardless.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This gets you really, really close.
... | timechart count
| eventstats count AS buckets first(_time) as first last(_time) as last
| eval spanSeconds=round((last-first - 1)/buckets)
You can after that ... | fields - count, first, last if you want, or ... | fieldformat span = strftime(spanSeconds, "%H:%M:%S") (Maybe)
It's only a guesstimate - there may be a way to get it better, but that should be really close anyway.
Happy Splunking!
-Rich
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
use @richfez 's answer to create the fields you need and in the simpleXML add
<eval token="bucket">strftime(first,"%Y/%m/%d")+"-"+strftime(last,"%Y/%m/%d")</eval> to create a token that should display the dates, add %H:%M:%S if you need timestamps.
use $bucket$ in the panel description/title to display the range the single value is displayed for.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am afraid I am looking for the duration of each bucket span, no the span of the entire search 😞