Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Dashboards & Visualizations
- :
- Splunk stats command to get total count of existin...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have an index that has vulnerabilities that are affecting hosts.
index=vulnerabilities
Fields in the index are:
host, VulnID, VulnName
I have a lookup name Assets. It has field name DNS. This field DNS is to be used as host in index's query. e.g.
index=vulnerabilities
| stats .........
| lookup Assets DNS AS host .....
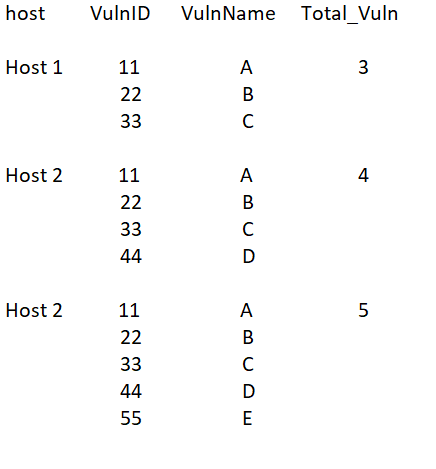
I need a query that gives me attached image results with fast performance because I have a lot of affected hosts with a lot of vulnerabilities. I will be using this query to create a scheduled report so I can reference this report in my dashboard to create panels. My query will be looking at a few days back based on my scans:
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What about this: your current query | stats list(VulnID) as VulnID list(VulnName) as VulnName count(VulnID) by host
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What about this: your current query | stats list(VulnID) as VulnID list(VulnName) as VulnName count(VulnID) by host
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @chrisyoungerjds,
With minor change, it all worked out. Instead of list, I used values and got desired output!! THANKS!