Are you a member of the Splunk Community?
- Find Answers
- :
- Apps & Add-ons
- :
- All Apps and Add-ons
- :
- Re: I have Configured AWS add-on in Heavy Forwarde...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have Configured Distributed Splunk Setup AWS add-on in Heavy Forwarder and AWS app in Search Head but Configuration changes not displaying AWS app dashboard
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Vardhan Thank you so much for your time I am really happy
here are the steps find the result
1.Install Splunk AWS add-on in Search Head
2.Create outputs.conf in search head directory (/opt/Splunk/etc/apps/splunk_apps_aws/local/ vi output.conf)
3. Enter the following content in output.conf
([indexAndForward]
index = false # Turn off indexing on the search head
[tcpout]
defaultGroup = my_search_peers # Name of the search peer group
forwardedindex.filter.disable = true
indexAndForward = false
[tcpout:my_search_peers]
server=10.10.10.1:9997,10.10.10.2:9997,10.10.10.3:9997 # list of peers)
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Vardhan Thank you so much, Vishnu without your help I can't the solution
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Vardhan Thank you so much for your time I am really happy
here are the steps find the result
1.Install Splunk AWS add-on in Search Head
2.Create outputs.conf in search head directory (/opt/Splunk/etc/apps/splunk_apps_aws/local/ vi output.conf)
3. Enter the following content in output.conf
([indexAndForward]
index = false # Turn off indexing on the search head
[tcpout]
defaultGroup = my_search_peers # Name of the search peer group
forwardedindex.filter.disable = true
indexAndForward = false
[tcpout:my_search_peers]
server=10.10.10.1:9997,10.10.10.2:9997,10.10.10.3:9997 # list of peers)
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
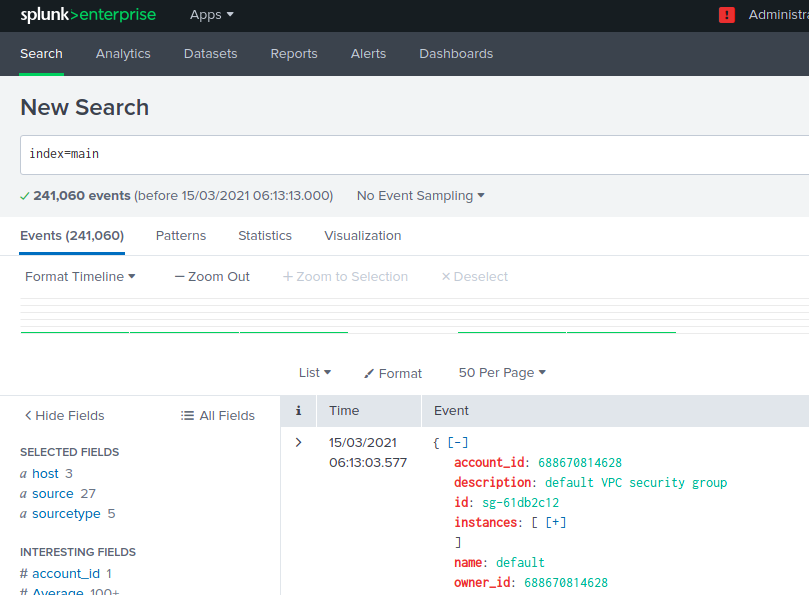
Whether logs are coming to index?
If logs are coming then I believe the app is not fetching the logs from correct index.Just check the default config of app is anywhere mentioned the index name in macro or eventtype.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Please check in macro.conf is there any other index name is mentioned.
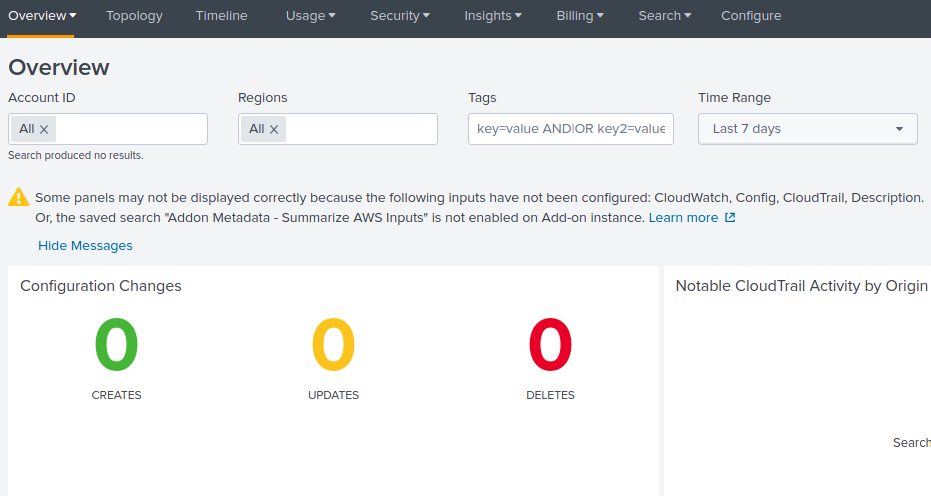
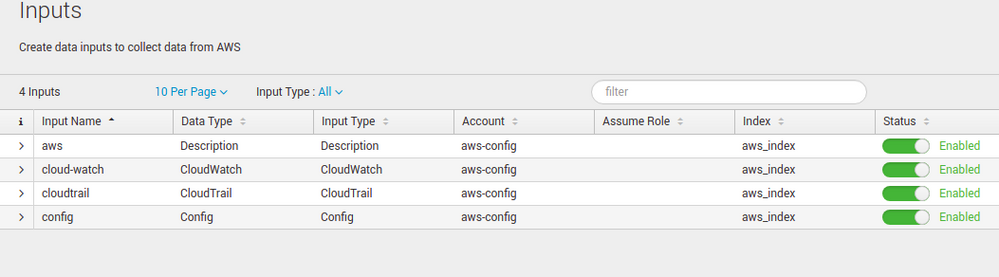
And also in the below screenshot shows the warning like the required inputs has not been configured. You may get the data from the aws.But that data may not be useful for the app.
So enable the below mentioned inputs in the hf and get those logs to the index.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
My Index name (aws_index) configured in the indexer cluster:
My Heavy Forwarder (Deployed in AWS add-on ) configuration:
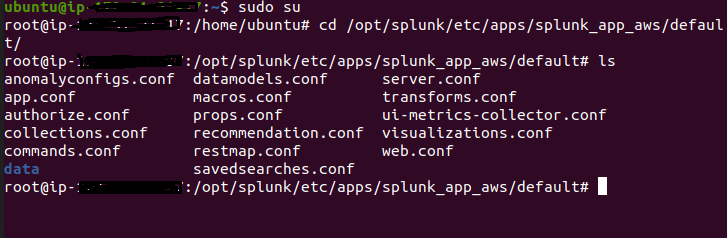
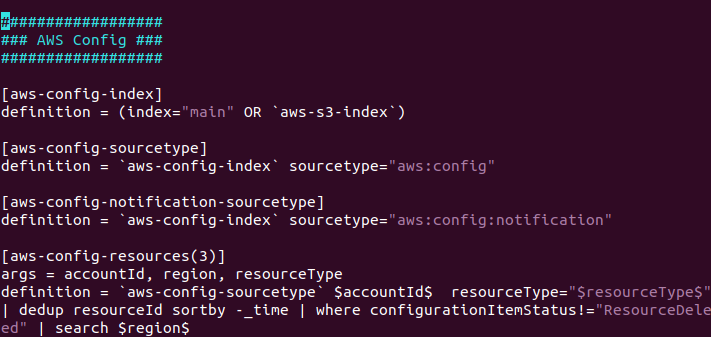
macro.conf file:
macro. conf file is correct or wrong?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
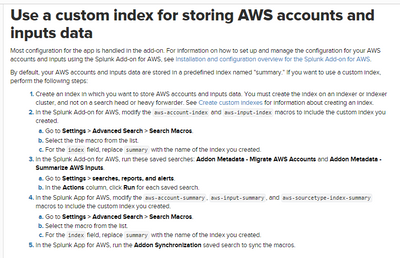
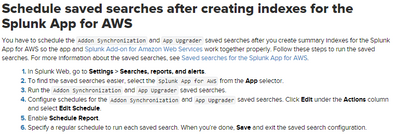
Can you follow the below steps given in the document. The Macro is using the Aws indexes and you need to replace all with custom indexes which you have created for aws logs.
https://docs.splunk.com/Documentation/AWS/6.0.2/Installation/Useacustomindex
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes @Vardhan
This article really helpful
but the result didn't any change
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In the Splunk Add-on for AWS, modify the aws-account-index and aws-input-index macros to include the custom index you created.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for response @isoutamo