Are you a member of the Splunk Community?
- Find Answers
- :
- Apps & Add-ons
- :
- All Apps and Add-ons
- :
- DateParserVerbose issue for Symantec Email Securit...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
DateParserVerbose issue for Symantec Email Security Add-on for Splunk
Hi All,
We are observing high number of parsing issues on sourcetype= symantec:email:cloud:atp. We haven't done any changes in Add-on. Please suggest how to resolve this issue. how to identify exact which events are facing this issue and how to resolve it.
Failed to parse timestamp in first MAX_TIMESTAMP_LOOKAHEAD (128) characters of event. Defaulting to timestamp of previous event (Wed Jun 29 10:52:21 2022). Context: source=/opt/splunk/etc/apps/TA-symantec_email/bin/symantec_collect_atp.py|host=s|symantec:email:cloud:atp|
06-29-2022 10:53:30.862 +0000 WARN DateParserVerbose [27921 merging] - The TIME_FORMAT specified is matching timestamps (INVALID_TIME (1656499945449)) outside of the acceptable time window. If this timestamp is correct, consider adjusting MAX_DAYS_AGO and MAX_DAYS_HENCE. Context: source=/opt/splunk/etc/apps/TA-symantec_email/bin/symantec_collect_atp.py|host=|symantec:email:cloud:atp|
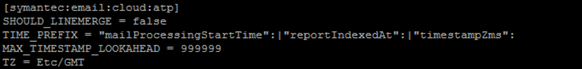
Please find the props.config file setting for symantec:email:cloud:atp
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content