Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Regex Source and Destination files with path, file...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I need some help with this one since it is beyond my regex skills which are not the best. I would have used the field extractor but the data does not show up to extract. The data comes from a tool called Varonis DatAlert and is stored in the Windows Event log and we want to be able to use this for custom Ransomware alerting.
The field from the Windows Event log called Additional_Data and I would like to extract it into 6 fields.
Additional_Data Sample
I:\Dept3\folder1\folder two\folder 3\folder 4\Filename1.htm changed to I:\Dept3\folder1\folder two\folder 3\folder 4\Filename1.txt
Desired Fields
source_path = I:\Dept3\folder1\folder two\folder 3\folder 4
source_file = Filename1.htm
source_type = htm
dest_path = I:\Dept3\folder1\folder two\folder 3\folder 4
dest_file = Filename1.txt
dest_type = txt
Thanks in advance
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It should be something like this if I'm not mistaken:
| rex field=Additional_Data "^(?<source_path>.+?)\\\(?<source_file>[^\\\]+) changed to (?<dest_path>.+?)\\\(?<dest_file>[^\\\]+)$"
| rex field=source_file "\.(?<source_type>[^\.]+)$"
| rex field=dest_file "\.(?<dest_type>[^\.]+)$"
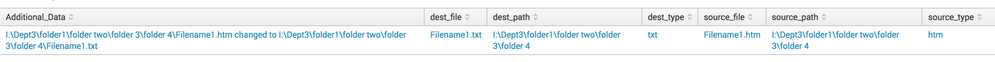
This is the way I tested it in my lab:
| stats count | fields - count
| eval Additional_Data ="I:\\Dept3\\folder1\\folder two\\folder 3\\folder 4\\Filename1.htm changed to I:\\Dept3\\folder1\\folder two\\folder 3\\folder 4\\Filename1.txt"
| rex field=Additional_Data "^(?<source_path>.+?)\\\(?<source_file>[^\\\]+) changed to (?<dest_path>.+?)\\\(?<dest_file>[^\\\]+)$"
| rex field=source_file "\.(?<source_type>[^\.]+)$"
| rex field=dest_file "\.(?<dest_type>[^\.]+)$"
Output (see picture below):
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you so much for all the answers you guys are awesome.
I have one of them working right now and have tested a couple of the others but was not able to get them fully working yet. I will go through all of them after work.
I do like the props and transforms as well but based on two of my tests it did not work yet and I'm probably doing something wrong. I used them in my app on the search head but the fields did not show up and I have not tried to troubleshoot it yet.
Once again, thanks!!!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Since you want to extract this field from an existing field (Additional_Data), you'd have to to use Field Transforms.
May something like this would work
props.conf (on Search Head)
[yourWinEventLogsourcetype]
REPORT-fromadditionaldata = additional_data_fields
transforms.conf (on Search Head)
[additional_data_fields]
SOURCE_KEY = Additional_Data
REGEX = (?<source_path>.+\\\(?<source_file>[^\.]+)\.(?<source_type>\S+)) changed to (?<dest_path>.+\\\(?<dest_file>[^\.]+)\.(?<dest_type>\S+)
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This works with your sample data.
... | rex field=Additional_Data "(?<source_path>.*?)\\(?<source_file>[^ ]+\.(?<source_type>\w+)) changed to (?<dest_path>.*)\\(?<dest_file>.+?\.(?<dest_type>\w+))$" | ...
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
can you try below:
yourBaseQuery
| rex field=Additional_Data "(?<source_path>.*\\)(?<sFileName>[^\.]+)\.(?<source_type>[^\s]+)\schanged\sto\s(?<dest_path>.*\\)(?<dFileName>[^\.]+)\.(?<dest_type>[^\s]+)"
| eval source_file=sFileName.".".source_type
|eval dest_file=dFileName.".".dest_type
| table Additional_Data, source_path, source_file, source_type, dest_path, dest_file, dest_type
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It should be something like this if I'm not mistaken:
| rex field=Additional_Data "^(?<source_path>.+?)\\\(?<source_file>[^\\\]+) changed to (?<dest_path>.+?)\\\(?<dest_file>[^\\\]+)$"
| rex field=source_file "\.(?<source_type>[^\.]+)$"
| rex field=dest_file "\.(?<dest_type>[^\.]+)$"
This is the way I tested it in my lab:
| stats count | fields - count
| eval Additional_Data ="I:\\Dept3\\folder1\\folder two\\folder 3\\folder 4\\Filename1.htm changed to I:\\Dept3\\folder1\\folder two\\folder 3\\folder 4\\Filename1.txt"
| rex field=Additional_Data "^(?<source_path>.+?)\\\(?<source_file>[^\\\]+) changed to (?<dest_path>.+?)\\\(?<dest_file>[^\\\]+)$"
| rex field=source_file "\.(?<source_type>[^\.]+)$"
| rex field=dest_file "\.(?<dest_type>[^\.]+)$"
Output (see picture below):
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks worked first try.