Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: same field name exists in two indexes but with...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
same field name exists in two indexes but with different values
Hola splunker.
i performed a search using two indexes, but these tow indexes have different fields that uses the same field name, for example:
EmailServer: has the filed name message_subject
EmailProxy: has the filed name message_subject
i want to search using the message_subject from the EmailServer
index=EmailServer OR index=EmailProxy NOT (src_ip=10.0.0.0/8 OR src_ip=192.168.0.0/16 OR src_ip=172.16.0.0/12 ) | table src_ip sender EmailServer.message_subject
Thanks ^_^^
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
index=EmailServer OR index=EmailProxy NOT (src_ip=10.0.0.0/8 OR src_ip=192.168.0.0/16 OR src_ip=172.16.0.0/12 )
| eval "EmailServer.message_subject"=if(index="EmailServer",message_subject,null)
| table src_ip sender EmailServer.message_subject- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the answer Whisperer ^_^
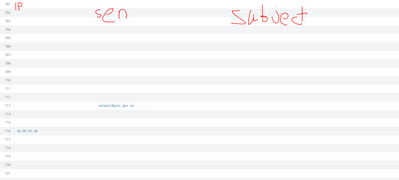
this is the result i got:
i forgot to tell you something, the src_ip field only exists at the EmailProxy, so the field sender is mutual,
so i want the stats to have:
EmailProxy.src_ip /// EmailServer.sender /// EmailServer.message_subject.
Thanks^_^
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
index=EmailServer OR index=EmailProxy NOT (src_ip=10.0.0.0/8 OR src_ip=192.168.0.0/16 OR src_ip=172.16.0.0/12 )
| eventstats values(src_ip) as "EmailProxy.src_ip" by sender
| eval "EmailServer.message_subject"=if(index="EmailServer",message_subject,null)
| table EmailProxy.src_ip sender EmailServer.message_subject- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
w'ere getting close !
unfortunately the src_ip field is null:
also the are empty records/Almost empty records:
thanks so much for your time, i really appreciate it, please help with this one
^_^
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you clarify that the proxy will have events for user and src_ip and the server will have events for the user and subject, i.e. the exact same value for user exists in both sets of events? If not, how are you trying to correlate events from the two indexes?