Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Splunk Search
×
Join the Conversation
Without signing in, you're just watching from the sidelines. Sign in or Register to connect, share, and be part of the Splunk Community.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: Why is my chart not displaying all field value...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
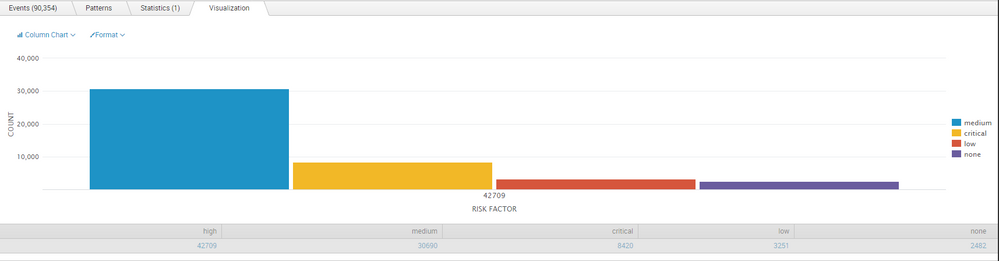
Why is my chart not displaying all field values?
rkaakaty
Path Finder
06-29-2017
10:26 AM
Hello,
My chart for some reason, isn't displaying the value "high" and it has the high count at the bottom of the graph when I want the count of the other types under the columns.
Here is my code:
index=nessus
| stats count(eval(risk_factor ="high")) as high count(eval(risk_factor ="medium")) as medium count(eval(risk_factor ="critical")) as critical count(eval(risk_factor ="low")) as low count(eval(risk_factor ="none")) as none
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
DalJeanis
Legend
06-29-2017
12:29 PM
Try setting the visualization barchart format-
format - general - show data values - on
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
woodcock
Esteemed Legend
06-29-2017
12:27 PM
Why not just do this:
index=nessus | stats count BY risk_factor
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
DalJeanis
Legend
06-29-2017
12:31 PM
Not the answer to the question he asked, but a great answer nonetheless.
Get Updates on the Splunk Community!
Data Management Digest – December 2025
Welcome to the December edition of Data Management Digest!
As we continue our journey of data innovation, the ...
Index This | What is broken 80% of the time by February?
December 2025 Edition
Hayyy Splunk Education Enthusiasts and the Eternally Curious!
We’re back with this ...
Unlock Faster Time-to-Value on Edge and Ingest Processor with New SPL2 Pipeline ...
Hello Splunk Community,
We're thrilled to share an exciting update that will help you manage your data more ...