- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Why is mvexpand not extracting all key/value pairs...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
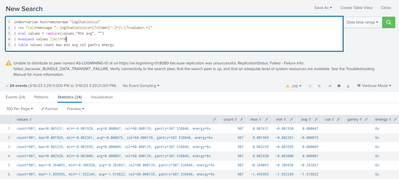
I am trying to expand multiple fields from specific log lines using mvexpand but for some strange reason some fields are not extracted as expected, see screenshot for an example:
I would also like to have the key/value pairs for col and gantry.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The max_match option is relevant because its absence tells me we're not dealing with a mutli-value field and so the mvexpand command is not of use.
To get each component of the values field into its own field we need to parse it. There is the extract command, but it only works with _raw so we have to jump through some hoops to use it.
<<your search to extract the values field>>
| eval _raw = values
| extract pairdelim=, kvdelim==
| table values count max min avg col gantry energy
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is not an mvexpand problem because the values field is not a multi-value field. We know it can't be a multi-value field because the rex command does not use the max_match option, which means only the first match of the regex will be extracted.
The fields that were extracted probably are the result of automatic extraction because they're in key=value format. I can't explain why the col and gantry fields were not extracted.
What is the end goal of this query? The mvexpand command puts each value of a multi-value field into a new event - is that what is desired?
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@richgalloway wrote:We know it can't be a multi-value field because the rex command does not use the max_match option, which means only the first match of the regex will be extracted.
I don't see why the regex here is such a proof. The `rex` is used to extract two named fields, of which the latter contains the values I am after and is assigned to values. I see no reason why `max_match` is even relevant here.
@richgalloway wrote:What is the end goal of this query? The mvexpand command puts each value of a multi-value field into a new event - is that what is desired?
The end goal is to extract all values (as per column headings from the results in my screenshot) from value field extracted using the regular expression and assigning them to the event so I can process and plot these values.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The max_match option is relevant because its absence tells me we're not dealing with a mutli-value field and so the mvexpand command is not of use.
To get each component of the values field into its own field we need to parse it. There is the extract command, but it only works with _raw so we have to jump through some hoops to use it.
<<your search to extract the values field>>
| eval _raw = values
| extract pairdelim=, kvdelim==
| table values count max min avg col gantry energy
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I had indeed resolved it using in the mean time:
| extract pairdelim="," kvdelim="=" clean_keys=t