- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Why does tstats command alter time stamps when I r...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am wondering why tstats command alters time stamps when I run it by _time.
| tstats values(text_len) as text_len values(ts) as ts where index = data sourcetype = cdr by _time thread_id num_attempts
raw data in index=data :
| Time | _time | 2023-03-22T13:14:16.000+01:00 |
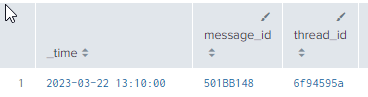
After tstats:
2023-03-22 13:10:00
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
To group events by _time, tstats rounds the _time value down to create groups based on the specified span. If no span is specified, tstats will pick one that fits best in the time window search - 10 minutes in this case.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
To group events by _time, tstats rounds the _time value down to create groups based on the specified span. If no span is specified, tstats will pick one that fits best in the time window search - 10 minutes in this case.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I ran into the same thing, but I noticed that when I run my queries against a data model that is not accellerated, I get the right results.
Is there a reason why running against a datamodel that is accelerated and the same data model that is not accelerated yield different results?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This thread is more than a year old so you are more likely to get responses by submitting a new question.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for your response. But in my case there are no groups, because i used also another field (id) in by section, which is unique. So I expected to see all events with their original timestamps.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
tstats by _time supports the span= argument, so you can do span=1s to get the a 1 second bucket of _time
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @LIS
@richgalloway is correct, it's due to grouping by the _time field.
If you do want to pull the original _time out of the event then do not group by _time but pull it out as a field value, e.g.
| tstats max(_time) AS _time values(text_len) as text_len values(ts) as ts where index = data sourcetype = cdr by thread_id num_attempts This assumes that each event has a unique thread_id and num_attempts, but hopefully this demonstrates the difference in what you expected.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
tstats still would have modified the timestamps in anticipation of creating groups. It wouldn't know that would fail until it was too late.
If this was a stats command then you could copy _time to another field for grouping, but I don't know of a way to do that with tstats.
If this reply helps you, Karma would be appreciated.