Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: Why can't I get my search results to sort prop...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
I have this search
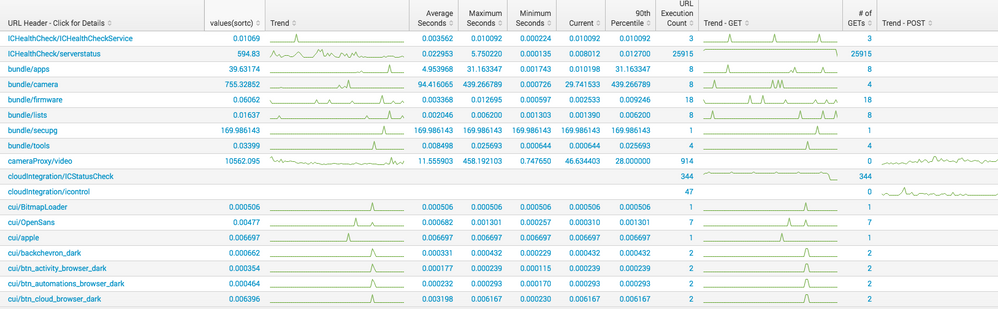
index=main | rex "(?i)\".*? /(?P<URL_HEADER>\w+/\w+)"| rex "(?i) UCT\-(?P<URL_MICRO_SECONDS>\d+)"|rex "(GET)(?<statusget>)"|rex "(POST)(?<statuspost>)"|eval seconds=URL_MICRO_SECONDS/1000000|eventstats avg(seconds) as avgseconds by URL_HEADER|eventstats count(URL_HEADER) as urlcount by URL_HEADER|eval sortc=avgseconds*urlcount|chart values(sortc) sparkline(avg(seconds)) as Trend avg(seconds) as "Average Seconds" max(seconds) as "Maximum Seconds" min(seconds) as "Minimum Seconds" last(seconds) as Current perc90(seconds) as "90th Percentile" count(URL_HEADER) as "URL Execution Count" sparkline(count(statusget)) as "Trend - GET" count(statusget) as "# of GETs" sparkline(count(statuspost)) as "Trend - POST" count(statuspost) as "# of POSTs" by URL_HEADER|sort sortc|rename URL_HEADER as "URL Header - Click for Details"
And for whatever reason I cannot get it to sort on the sortc value. I get results that look like this.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You don't have a field called sortc after the chart command. You only have a field called values(sortc) You should either change to sort values(sortc) OR in your chart command alias the fieldname values(sortc) as sortc.
Just on a different note, you should be able to combine your two eventstats in to one. eventstats avg(seconds) as avgseconds count(URL_HEADER) as urlcount by URL_HEADER
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You don't have a field called sortc after the chart command. You only have a field called values(sortc) You should either change to sort values(sortc) OR in your chart command alias the fieldname values(sortc) as sortc.
Just on a different note, you should be able to combine your two eventstats in to one. eventstats avg(seconds) as avgseconds count(URL_HEADER) as urlcount by URL_HEADER
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Sundareshr!
Ahhhh I wasn't aware that by using values(sortc) it actually changes the field name from sortc to "values(sortc)" interesting.
Thanks for the update on the eventstats!