Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Why am I getting different results for the same se...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
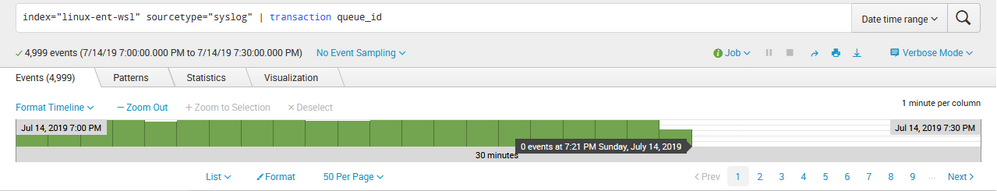
If I run the same search using two different time windows I consistently get different results.
I'm looking to count the number of email messages sent. The search query is simple:
index="linux" sourcetype="syslog" | transaction queue_id
When i search for a time range of 19:00:00 to 19:30:00 I get the following results (note from 19:21 on there are zero results):
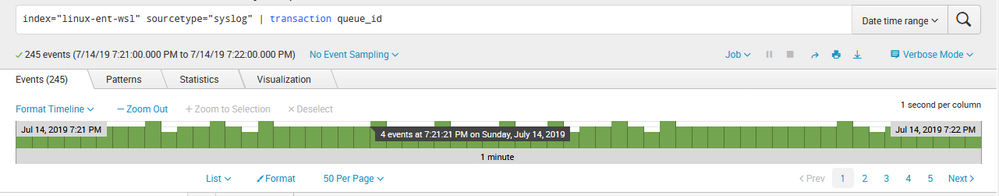
If I then search for 19:21:00 to 19:22:00 I get the following results (note: now where are 245 events):
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Because transaction is a command that consumes a HUGE amount of RAM and when scaled to any practical time-window will exhaust all RAM available to you and your search and WILL SILENTLY ABORT yielding partial results and NO INDICATION THAT HAPPENED (unless you Inspect your job and check the search.log). This is the main reason that I am constantly harping: DO NOT USE transaction! So don't use it.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Adding to what Woodcock said above, I've found transaction can be replaced by stats in most situations with a little extra effort. Obviously it depends on what you're trying to report on, but something like this:
index=linux sourcetype=syslog
| stats last(somefield) as last_something first(somefield) as first_something range(_time) as span by queue_id
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Because transaction is a command that consumes a HUGE amount of RAM and when scaled to any practical time-window will exhaust all RAM available to you and your search and WILL SILENTLY ABORT yielding partial results and NO INDICATION THAT HAPPENED (unless you Inspect your job and check the search.log). This is the main reason that I am constantly harping: DO NOT USE transaction! So don't use it.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Per your instruction I took a look at Inspector (should have done this originally) and it does indicate: "Some transactions have been discarded. To include them, add keepevicted=true.
Adding that to the query does in fact resolve the issue.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Even so, do not use transaction; take the time and effort to use *stats.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So that's good to know. I'll inspect the job and look into search.log for more details.
Two questions then:
If I can't use transaction to group multiple events then what do I use?
My single-instance Splunk Enterprise server has 256GB of memory and appears to use very little of that memory. Am I really exhausting resources?