Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Splunk Search
×
Are you a member of the Splunk Community?
Sign in or Register with your Splunk account to get your questions answered, access valuable resources and connect with experts!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: Using stats dc with stats list and count
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
jwalzerpitt
Influencer
01-16-2019
11:23 AM
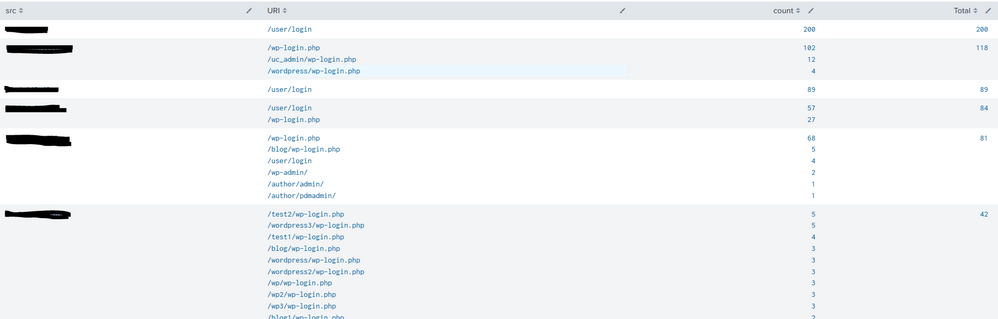
I have the following search looking for external hosts that are trying to brute force multiple WordPress or Drupal sites:
index=foo sourcetype="f5:bigip:asm:syslog" action!=blocked uri="/*login.php" OR uri="/*admin/" OR uri="*user\/login" uri!="*revslider*" action!=blocked
| stats count by src uri
| sort -count
| stats list(uri) as URI, list(count) as count, sum(count) as Total by src
| sort -Total
| head 10
Output is as follows:
How can I utilize stats dc to return only those results that have >5 URIs?
Thx
1 Solution
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
vnravikumar
Champion
01-16-2019
12:18 PM
Hi @jwalzerpitt
Please try
| stats dc(uri) as distinct_uri, values(uri) as URI, values(count) as count, sum(count) as Total by src | where distinct_uri > 5
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
vnravikumar
Champion
01-16-2019
12:18 PM
Hi @jwalzerpitt
Please try
| stats dc(uri) as distinct_uri, values(uri) as URI, values(count) as count, sum(count) as Total by src | where distinct_uri > 5
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
jwalzerpitt
Influencer
01-16-2019
12:31 PM
Thx as that worked perfectly!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
vnravikumar
Champion
01-16-2019
12:32 PM
welcome 🙂
Get Updates on the Splunk Community!
Observe and Secure All Apps with Splunk
Join Us for Our Next Tech Talk: Observe and Secure All Apps with SplunkAs organizations continue to innovate ...
Splunk Decoded: Business Transactions vs Business IQ
It’s the morning of Black Friday, and your e-commerce site is handling 10x normal traffic. Orders are flowing, ...
Fastest way to demo Observability
I’ve been having a lot of fun learning about Kubernetes and Observability. I set myself an interesting ...