- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Splunk App for Windows Infrastructure: Receiving d...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Splunk App for Windows Infrastructure: Receiving different results from directories
Hi,
For some reason when running one of the preset Active Directory searches like 'Group Changes' for instance I do not seem to get results but when I run the same thing under the report "Active Directory Update Group Lookup" I seem to get results that I could not find using the Active Directory search.
I've accompanied screenshots of what I am facing:
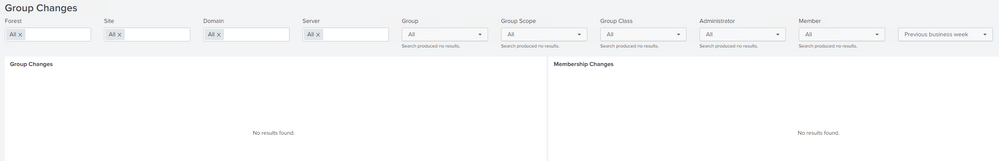
This is what I am getting when using the Active Directory Search. Note the "Previous business week" Search scope (on the rightmost part)
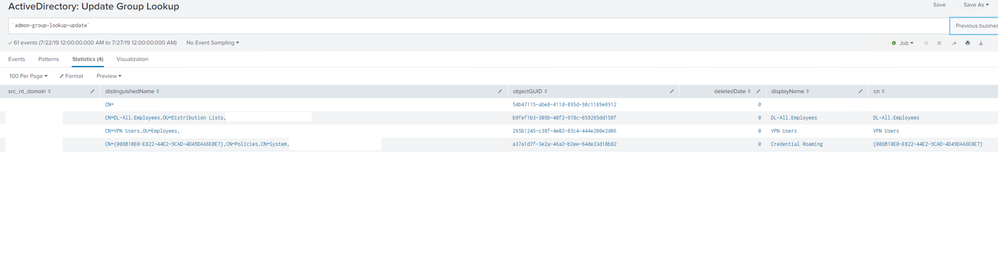
This is running the same kind of lookup using the Core Views report named "Active Directory: Update Group Lookup" (performing the same Search scope of 'Previous business week'
Shouldn't I get the same results in both of them? The reason why I want to see it in the first search is that I want to see the changes (the accounts added/removed) instead of it just telling me what groups had a change with no further details in the second search.
If anyone has any insight why the 'Group Changes' search does not work or produce the results I want
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I believe each of those panels will allow you to look at the full Search string. I would start there and see what the differences are between the two searches, it may just be a simple update to a field on the first panel.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Nahra,
I went ahead and did what you suggested, so for the the one that is working you can see it in the screenshot:
`admon-group-lookup-update'
The search commands for the two panels in the 'Group Changes' AD search are very different from the report version I think this is because there is much more detail in terms of what members were added/removed:
eventtype=msad-group-changes (host="") user_group="" MSADGroupType="" MSADGroupClass=""|eval adminuser=src_nt_domain."\".src_user|search adminuser="*"|table _time,adminuser,msad_action,MSADGroupClass,MSADGroupType,src_nt_domain,user_group|rename adminuser as "Administrator",msad_action as "Action",user_group as "Group", MSADGroupClass as "Type", MSADGroupType as "Scope",src_nt_domain as "Domain"
This one is for the "Group Changes" panel
eventtype=msad-groupmembership-changes (host="") user_group="" MSADGroupType="" MSADGroupClass="" member="" | eval adminuser=src_nt_domain."\".src_user | search adminuser="" | table _time,adminuser,MSADGroupClass,MSADGroupType,src_nt_domain,user_group,msad_action,member | rename adminuser as "Administrator",MSADGroupClass as "Type",MSADGroupType as "Scope",src_nt_domain as "Domain",user_group as "Group",msad_action as "Action",member as "Member"
This one is for the "Membership Changes" panel
I also looked up the eventtype=msad-groupmembership-changes and eventtype=msad-group-changes and confirmed those event types do exist as well. I performed searches based on those event IDs too and was able to pull data.