Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- REX Extract and/or separate a single field into 1 ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
REX Extract and/or separate a single field into 1 or 2 fields based on different patterns
Need to extract or split a filed value into different fields based on a condition/irregular pattern(or however it can be called).
Attached is what I tried but it did not work.
Expected output:
MeterName field should be separted into one or two fields based on the field value and pattern. / works as a separator wherever exixts. The text "Low Priority" if exists, should be ignored.
Possible source field value patterns and Expected extraction output :
Pattern 1 : "single alphanumeric word" = Should be MeterName1
Pattern 2: "multiple alphanumeric words separated by space" = MeterName1
Pattern 3 : "single alphanumeric word" -space- Low priority = MeterName1 (while "* -space- Low priority*" ignored)
Pattern 4: "multiple alphanumeric words separated by space" -space- Low priority = MeterName1 (while "-space- Low priority" ignored)
Pattern 5 : "single alphanumeric word or multiple words separated by space" / "single alphanumeric word or multiple words separated by space" = MeterName1 / MeterName2
Pattern 6 : "single alphanumeric word or multiple words separated by space" / "single alphanumeric word or multiple words separated by space" -space- Low priority = MeterName1 / MeterName2 (while "-space- Low priority" ignored)
Tried few other but again not the required output:
| rex field=MeterName "^(?\w+\s\w+)\/(?\w+).*$"
= > Matched only one entry, with result - MeterName = E20 v3/E20s v3 Low Priority MeterName1 =E20 v3 MeterName2 = E20s
| rex field=MeterName "^(?\w+\s\w+)\/(?\w+.*)$"
= > Matched only one entry, with result - MeterName = E20 v3/E20s v3 Low Priority MeterName1 =E20 v3 MeterName2 = E20s v3 Low Priority
Can someone please help me achieve the expected result?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nobody is going to be able to help you when you post pictures. We need text so that we can work with it in our Splunk Search Heads.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
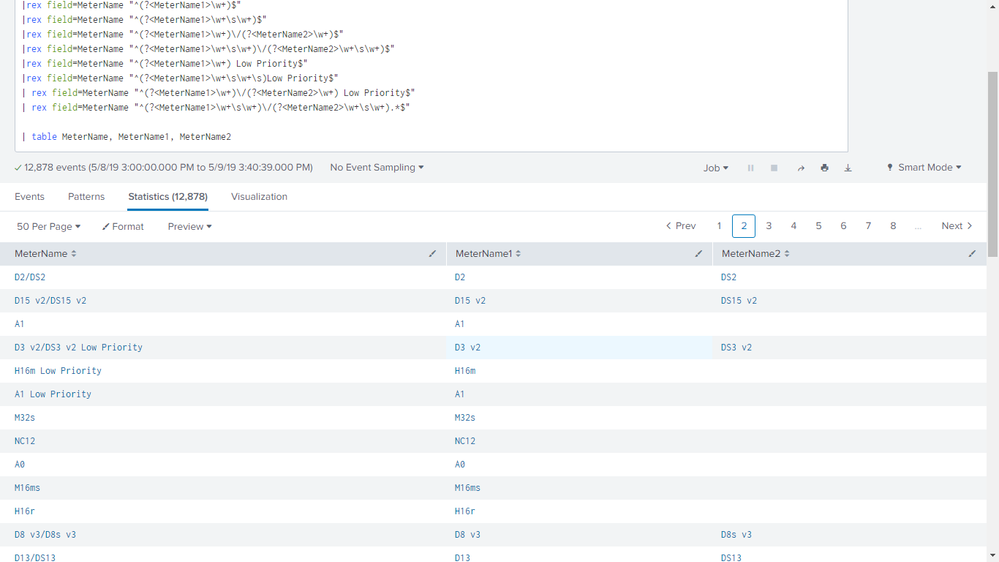
While trying around, I finally found a way of putting rex commands in multiple different formats that together served my requirement. However, I feel it may not be the right way of writing it. Hence please help me fine tune and reduce/optimize the code.
Here's the code and the output:
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you are doing RegEx on the same source filed, then you can do this:
... | rex field=foo "(?:RegEx1)|(?:RegEx2)|(?:RegEx3)|(?:RegEx4)|(?:RegEx5)|(?:RegEx6)"