Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Need help in developing splunk query
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Need help in developing splunk query
Hi All,
2021-07-12 09:33:20,659 - daemons.save_claim_dex.src.__main__ - INFO - Skill='SAVE_CLAIM_INFO', message='skill execution info', ActivationId='3b660cbf-77c0-4999-a76c-aca5833aa3ca', Method='POST', TxnStatus='SUCCESS', StatusCode='200', TxnTimeTaken='34.358', StartTimestamp='1626082400.624848', EndTimestamp='1626082400.659206', TxnStartTime='2021-07-12T09:33:20.624848', TxnEndTime='2021-07-12T09:33:20.659206'
2021-07-12 09:33:20,582 - daemons.dex_gen_resp.src.__main__ - INFO - Skill='DEX_GENERATE_RESPONSE', message='skill execution info', ActivationId='3b660cbf-77c0-4999-a76c-aca5833aa3ca', Method='POST', TxnStatus='SUCCESS', StatusCode='200', TxnTimeTaken='91.984', StartTimestamp='1626082400.490515', EndTimestamp='1626082400.582499', TxnStartTime='2021-07-12T09:33:20.490515', TxnEndTime='2021-07-12T09:33:20.582499'
2021-07-12 09:33:20,435 - daemons.save_claim_dex.src.__main__ - INFO - Skill='SAVE_CLAIM_INFO', message='skill execution info', ActivationId='3b660cbf-77c0-4999-a76c-aca5833aa3ca', Method='POST', TxnStatus='SUCCESS', StatusCode='200', TxnTimeTaken='49.063', StartTimestamp='1626082400.386638', EndTimestamp='1626082400.435701', TxnStartTime='2021-07-12T09:33:20.386638', TxnEndTime='2021-07-12T09:33:20.435701'
From the above log, I need two splunk queries.
1. trace the activationid which processed different skills, provide end to end response time which should include all the skills response times.
2. grouping info-skill fields response times [ex SAVE_CLAIM_INFO ,DEX_GENERATE_RESPONSE in table format]
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It looks like the total_time_tkn field doesn't exist. Is the strptime format correct? If you share a sample event we can help you check.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What have you tried so far? What results did you get?
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
"*3b660cbf-77c0-4999-a76c-aca5833aa3ca*"
| eval Date = date_month." ".date_mday
| eval Hour = date_hour
| eval start_time=strptime(StartTimestamp, "%FT%T.%3N")
| eval end_time=strptime(EndTimestamp, "%FT%T.%3N")
| eval total_time_tkn=round(((end_time-start_time) * 1000),0)
| rex field=_raw "INFO - Skill='(?.*?)',"
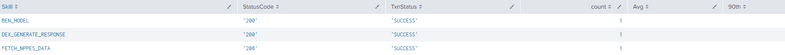
| stats count avg(total_time_tkn) as Avg p90(total_time_tkn) as 90th by Skill StatusCode,TxnStatus
Below i don't see avg and 90thP. Also am adding activationid in the query. which i want to get in runtime.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
can anyone please help.
@gcusello