Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Splunk Search
×
Are you a member of the Splunk Community?
Sign in or Register with your Splunk account to get your questions answered, access valuable resources and connect with experts!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Line chart of daily event totals over N-days
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Line chart of daily event totals over N-days
scotmatson
Explorer
01-22-2019
07:16 AM
I need to display trending IP events over the course of 90 days with each day being a sum of the events.
My original query which was only interested in daily metrics on a more granular level uses stats > sort > addcoltotal. I need to retain the sorting behavior as I am only interested in the top-20 IPs currently. I've been able to get the daily totals I am interested in but I am not sure how to repeat the query across the 90 days and translate that into a timechart.
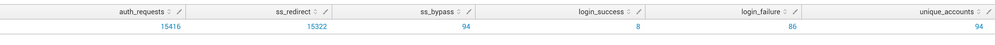
... base
| fields ip email username inf ssr
| stats count(ip) as ar count(ssr) as ssre count(eval(inf)) as ssby count(eval(inf="success")) as ls count(eval(inf="warning")) as lf dc(eval(coalesce(email, username))) as ua by ip
| sort 20 -ar
| stats sum(ar) as auth_requests sum(ssre) as ss_redirect sum(ssby) as ss_bypass sum(ls) as login_success sum(lf) as login_failure sum(ua) as unique_accounts
Career Survey
First 500 qualified respondents will receive a $20 gift card! Tell us about your professional Splunk journey.
Get Updates on the Splunk Community!
Tech Talk Recap | Mastering Threat Hunting
Mastering Threat HuntingDive into the world of threat hunting, exploring the key differences between ...
Observability for AI Applications: Troubleshooting Latency
If you’re working with proprietary company data, you’re probably going to have a locally hosted LLM or many ...
Splunk AI Assistant for SPL vs. ChatGPT: Which One is Better?
In the age of AI, every tool promises to make our lives easier. From summarizing content to writing code, ...