Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: I'm using timechart to produce two rows for tw...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm using timechart to produce two rows for two blocks of time, how can I do a count on only row 2 and not row 1?
Hello,
I set up an alert to search for an error message that appears in one my windows application. Time-wise I set it up to search the last 10 minutes only.
SourceName="My Web Client" Message="My Error Message" earliest=-11m@m latest=-1m@m
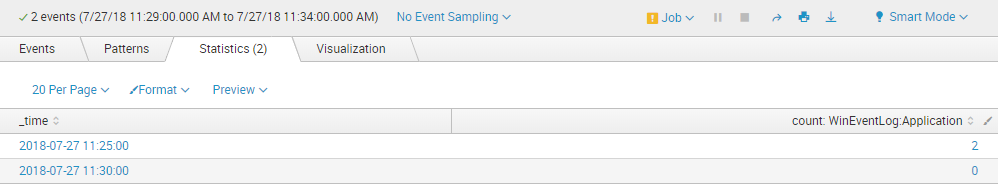
| timechart span=5m count values() BY source
Which produces this result (see image) :
This almost works for what I want. But, I want this to trigger an email to me only if the second row's count is = 0. Right now it alerts regardless of any number, including 0.
How do I declare that row2's count must be 0? row1 is allowed to be any count number it wants, but row2 must be 0, otherwise I do not want the alert to trigger.
Thanks,
Jeff
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Try this
SourceName="My Web Client" Message="My Error Message" earliest=-11m@m latest=-1m@m
| timechart span=5m count values() BY source
| eventstats list(count*) as list* | eval shouldAlert="No"
| foreach list* [| eval shouldAlert=if(mvindex('<<FIELD>>',1)==0,"Yes",shouldAlert) ]
| where shouldAlert="Yes"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
Line 3 was hepful, but line 4 causes this error:
Error in 'eval' command: Typechecking failed. The '==' operator received different types