Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: How would I configure my regex to also include...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How would I configure my regex to also include Windows data?
I have a query that will identify all the logs in my instance for a certain index, it list everything running except for Windows. What am i missing? thanks in advance.
index="source" | rex field=source "^.*\/(?=[^/])(?.*?)($|\s|\-|\_)"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Without seeing more of your data, it appears to me that you are not getting anything with a Windows drive letter. But if you can give more information about your index called "source", it would be easier to help answer the question.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
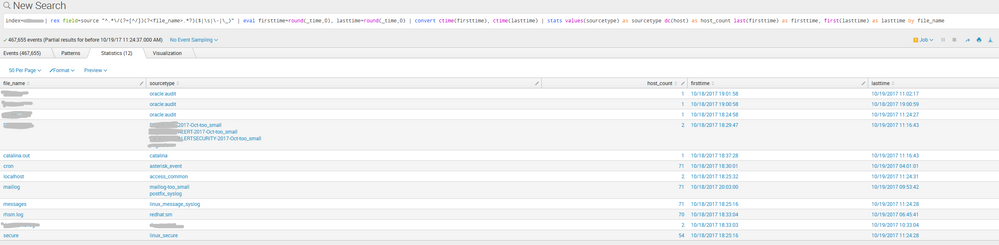
the screen shot is below
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
enclosed is the query and the result.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
index="source" | rex field=source "^.\/(?=[^/])(?.?)($|\s|-|_)" ...this is the whole regex
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you at least provide examples (even obfuscated) of the output of:
index="source" | table source
It should include something from several types, like linux, oracle, windows. Without that information I'm afraid I can't help out at all.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
well for privacy concerns i can only provided limited data, the query captures all data except Windows.
the index is not called source, i just used that as an example.
the other data sources it collects is - linux,oracle....etc.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Suggestion - we may be able to solve this here, but if not, then get yourself onto the splunk slack channel, where you can post the semi-confidential data privately in a direct message to someone, then delete it after solving your problem.
info here...
https://answers.splunk.com/answers/443734/is-there-a-splunk-slack-channel.html