Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How to use index time to search the data to avoid ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dear All,
I was going through a Splunk conf 21 where the narrator explained to use the index time instead of search time using a Macro
Out of curiosity, I went to understand the query and have the following doubts:-
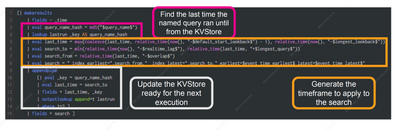
1) In row 5 of the query, What is "default start lookback" & "longest lookback" and from where they getting the value?
2) In row 6 of the query, What is "realtime lag" &" longest query" and from where they getting the value?
3) What is the concept of row 8? how the search is working?
4) What does row 14 mean? what is 1=2?
Please find below the splunk query
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
All of the variables surrounded by '$' (like $overlap$) are tokens. Tokens are set in the <input> section of a dashboard or are the results of other dashboard panels. They also can be passed in from another dashboard. Perhaps an earlier part of the talk describes this.
Line 8 is not performing a search - it's just building a search string using a combination of string literals and fields connected with the concatenation (.) operator.
Line 14 only passes events where 1=2, which is a way of ensuring the subsearch returns no results. IOW, it makes the outputlookup command silent.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
All of the variables surrounded by '$' (like $overlap$) are tokens. Tokens are set in the <input> section of a dashboard or are the results of other dashboard panels. They also can be passed in from another dashboard. Perhaps an earlier part of the talk describes this.
Line 8 is not performing a search - it's just building a search string using a combination of string literals and fields connected with the concatenation (.) operator.
Line 14 only passes events where 1=2, which is a way of ensuring the subsearch returns no results. IOW, it makes the outputlookup command silent.
If this reply helps you, Karma would be appreciated.