Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How to split search results into separate lines in...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi!
I did a search like this:
| tstats summariesonly=t count from datamodel=XZY WHERE field_ip="192.168.101" OR field_ip="192.168.102" OR field_ip="192.168.103" OR field_ip="192.168.104" OR field_ip="192.168.105" by field_ip, _time
But this shows me just one line and concatenates the single field values (the different IPs) after another... so the first "quarter of the line is the first IP the next quarter is the next IP also.
When I do the same search with the following:
| datamodel XZY search | search field_ip="192.168.101" OR field_ip="192.168.102" OR field_ip="192.168.103" OR field_ip="192.168.104" OR field_ip="192.168.105" | timechart count by field_ip
It does split the field_ip into its values and shows me 4 lines. One for each IP.
Due to performance issues, I would like to use the tstats command.
(I have the same issue when using the stats command instead of the timechart command)
So I guess there is something like a parameter I must give the stats command to split the result in different lines instead of concatenating the results.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
| tstats summariesonly=t count from datamodel=XZY WHERE field_ip="192.168.101" OR field_ip="192.168.102" OR field_ip="192.168.103" OR field_ip="192.168.104" OR field_ip="192.168.105" by _time, field_ip
| xyseries _time field_ip count
| fillnull "192.168.101" "192.168.102" "192.168.103" "192.168.104" "192.168.105"
I'm not sure about the span. so, I make this query. how about this?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
| tstats summariesonly=t count from datamodel=XZY WHERE field_ip="192.168.101" OR field_ip="192.168.102" OR field_ip="192.168.103" OR field_ip="192.168.104" OR field_ip="192.168.105" by _time, field_ip
| xyseries _time field_ip count
| fillnull "192.168.101" "192.168.102" "192.168.103" "192.168.104" "192.168.105"
I'm not sure about the span. so, I make this query. how about this?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Try combining tstats with timechart.
| tstats summariesonly=t prestats=t count from datamodel=XZY WHERE field_ip="192.168.101" OR field_ip="192.168.102" OR field_ip="192.168.103" OR field_ip="192.168.104" OR field_ip="192.168.105" by _time, field_ip
| timechart count by field_ip
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
first of all: Ups! I just noticed I missed an octet in the IP addressas... please imagine them like 192.168.1.10x
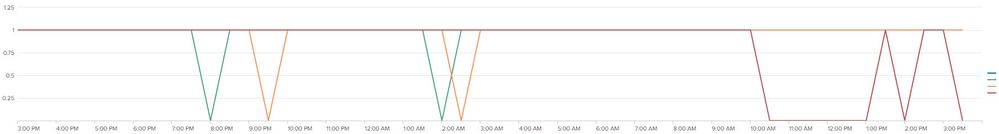
unfortunately this doesn't work as intended. When I do this it counts only the appearence of the field_ip value.
So for example if at time 11:30 192.168.1.103 has 400 counts, with the above query timechart shows me at 11:30 a value of 1 for 192.168.1.103...
The result I get is this: