Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Splunk Search
×
Are you a member of the Splunk Community?
Sign in or Register with your Splunk account to get your questions answered, access valuable resources and connect with experts!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: How to group by a column value
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to group by a column value
gautham
Explorer
08-23-2016
07:13 AM
Hi,
I'm searching for Windows Authentication logs and want to table activity of a user.
My Search query is :
index="win*" tag=authentication | stats values(src), values(dest), values(LogonType) by user | ....
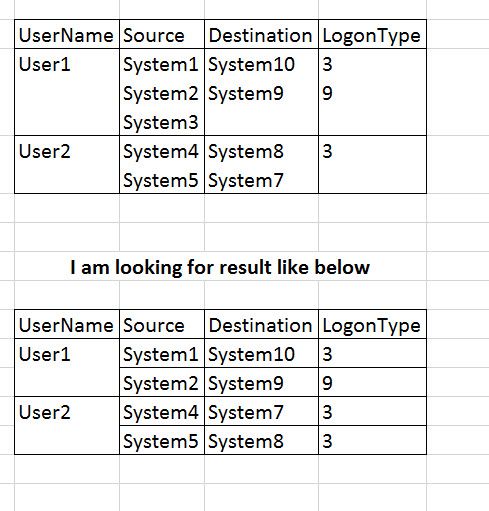
I get Results like this.
But i am looking for some
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
somesoni2
Revered Legend
08-24-2016
08:36 AM
Try like this
index="win*" tag=authentication src=* dest=* LogonType=* | stats values(src), values(dest), values(LogonType) by user
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
mhpark
Path Finder
08-24-2016
07:05 AM
have you tried this?
| transaction user | table user, src, dest, LogonType | ...
and if you don't want events with no dest,
you should add
dest=*
to your search query.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
pradeepkumarg
Influencer
08-23-2016
08:57 AM
index="win*" tag=authentication | stats values(user) by source,dest,LogonType | ....
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
gautham
Explorer
08-24-2016
06:45 AM
Thank you pradeep for your response.
But this search does not give the expected result. I do not want values(user) . I want unique value of User.
Get Updates on the Splunk Community!
Splunk Decoded: Service Maps vs Service Analyzer Tree View vs Flow Maps
It’s Monday morning, and your phone is buzzing with alert escalations – your customer-facing portal is running ...
What’s New in Splunk Observability – September 2025
What's NewWe are excited to announce the latest enhancements to Splunk Observability, designed to help ITOps ...
Fun with Regular Expression - multiples of nine
Fun with Regular Expression - multiples of nineThis challenge was first posted on Slack #regex channel ...