Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: Extract multiple hostname from one regex searc...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi everyone,
I'm trying to create a simple list with all the devices found on the logs from globalprotect. The deal is, i'm using rex to match it with regular expressions. I've already used regex101.com to double check my search but, when I run it on splunk it fails.
My search:
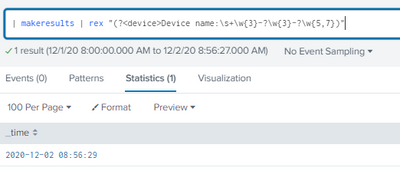
index="ind_Aaaabbbb" log_subtype="globalprotect" globalprotectgateway-config-succ OR globalprotectgateway-logout-succ
| rex field=_raw (?<device>\w\w\w\w\w\w\s\w\w\w\w:\s+(?:\w+\-\w+\-\w+|\w+))
| table _time, user, event_id, src_ip, device, dvc_name, dvc
The ideal expresions to capture:
Device name: DDD-AAA-BBBBB
Device name: DDDAAABBBBBBB
Error returned by Splunk:
Error in 'SearchParser': Missing a search command before '\'. Error at position '198' of search query 'search index="index" log_subtype="globalpro...{snipped} {errorcontext = -\w+\-\w+|\w+)) | tab}'.
Example data:
SYSTEM,globalprotect,0,2020/11/29,,globalprotectgateway-config-succ,Gateway-XXX-XX-XXX-N,0,0,general,informational,"GlobalProtect gateway client configuration generated. username.5, Private IP: 00.000.000.00, Client version: 5.1.1-12, Device name: DDD-AAA-BBBBB, Client OS version: Microsoft Windows 10 Pro , 64-bit, VPN type: Device Level VPN.",000...,0x0,0,0,0,0,,FW-PA-0000-AAA-CCC-TTTT
SYSTEM,globalprotect,0,2020/11/29 ,,globalprotectgateway-config-succ,Gateway-XXX-XX-N,0,0,general,informational,"GlobalProtect gateway client configuration generated. username.5, Private IP: 00.000.000.000, Client version: 5.1.5-20, Device name: DDDAAABBBBBBB, Client OS version: Microsoft Windows 10 Pro , 64-bit, VPN type: Device Level VPN.",000...,0x0,0,0,0,0,,FW-PA-0000-AAA-CCC-TTTT
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I suspect rex doesn't like the embedded pipe character. Try this query that not only doesn't use a pipe, it's also tons more efficient (51 steps vs. 3250).
(?<device>Device name:\s+\w{3}-?\w{3}-?\w{5,7})If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I suspect rex doesn't like the embedded pipe character. Try this query that not only doesn't use a pipe, it's also tons more efficient (51 steps vs. 3250).
(?<device>Device name:\s+\w{3}-?\w{3}-?\w{5,7})If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
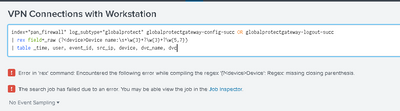
Hi @richgalloway unfortunately that search didn't help, It stills returning an error. This time its the following
Error in 'rex' command: Encountered the following error while compiling the regex '(?<device>Device': Regex: missing closing parenthesis.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No such error here. Please share your full query.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The rex command requires the regex be enclosed in quotation marks.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Perfect, it totally worked. Thank you very much!