- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: Compare value of 2 logfiles for notification
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi all,
I'm a beginner working with splunk. I have 2 Logfiles with the same Name, but from 2 different Hosts. I would like to compare both file for an expression (e.g. "server disconected") and only get the result, when the same expression is in both file in the sime time-period (last 10 min.) so that i could use the select for a notification.
I hope you understand what i mean🙂
Thanks, Simon
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @simon9,
sorry, I understood exactly the opposite!
with my search you count the number of different hosts, when the count is two, means that's present in both hosts.
please, try this:
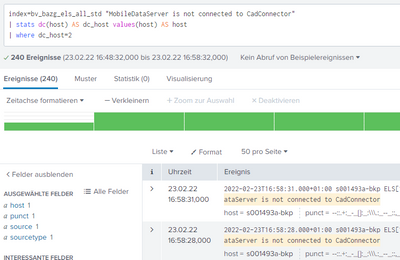
index=your_index source="yoursource" "server disconnected"
| stats dc(host) AS dc_host values(host) AS host
| where dc_host=2Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ciao @gcusello
thanks for your fast response! I tried it, but i get the data also if the entrie is just in one logfile . I need a result only, if the expression "server disconnect" is in both logfile at the same time.
e.g:
Logfile from "host 1" has 10 entrys "server disconnected" and logfile from "host 2" has 2 entrys "server disconnected" in the same timeperiod -> result should be 12.
Logfile from "host 1" has 10 entrys "server disconnected" and Logfile from "host 2" has 0 entrys "server disconnected" in the same timeperiod -> result would be 0.
Thanks, Simon
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @simon9,
sorry, I understood exactly the opposite!
with my search you count the number of different hosts, when the count is two, means that's present in both hosts.
please, try this:
index=your_index source="yoursource" "server disconnected"
| stats dc(host) AS dc_host values(host) AS host
| where dc_host=2Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@gcusello you don't need to apologize, my description was not the best !
I tried the new statement, but unfortunately i still get the result, althoug just 1 logfile (Host) has entrys.
Thank you for your Help!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @simon9,
you don't have results: the statistics tab is empty, you have two events from the same host,
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@gcusello OK, i understand. Grazie Mille for your help
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @simon9,
good for you, see next time!
Ciao and happy splunking.
Giuseppe
P.S.: Karma Points are appreciated 😉
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @simon9,
try something like this:
index=your_index source="yoursource" "server disconnected"
| stats dc(host) AS dc_host values(host) AS host
| where dc_host=1
| table hostCiao.
Giuseppe