Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: Decimal value comparison
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
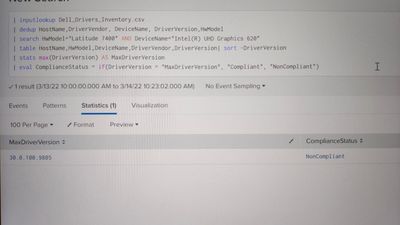
How to compare the result string having Decimal value?
Hi,
I'm unable to compare the result string which is having version(decimal value). While I'm using "If" condition it is not comparing.
In the above required output should be compliant... please help me with this.
Thanks.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How could I get the max version number from the input file ?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you want to get a version number out of the dotted version numbers, this is one example tecnique
| makeresults
| fields - _time
| eval versionNumber=split("30.0.100.9805,30.0.99.9805,2.10.0.60,1.90,2.17.0.9.53.176,172.3.4,172.3.40.199", ",")
| mvexpand versionNumber
| rex field=versionNumber "(?<t_v5>\d+)\.?((?<t_v4>\d+))?\.?((?<t_v3>\d+))?\.?((?<t_v2>\d+))?\.?((?<t_v1>\d+))?\.?((?<t_v0>\d+))?"
| foreach t_v* [ eval t_value=(pow(10, (<<MATCHSTR>>-3) * 3)) * <<FIELD>> + coalesce(t_value, 0) ]
| eval rounded_value=round(t_value, 9)
| sort t_value t_v5 t_v4 t_v3 t_v2 t_v1 t_v0
| table versionNumber t_value rounded_valueUp to the mvexpand is the example setup
What's useful for you is rex/foreach/eval 3 lines. t_value will give you a version number as a decimal number that can be compared numerically with other numbers, so for your case
Your search...
| rex field=DriverVersion "(?<t_v5>\d+)\.?((?<t_v4>\d+))?\.?((?<t_v3>\d+))?\.?((?<t_v2>\d+))?\.?((?<t_v1>\d+))?\.?((?<t_v0>\d+))?"
| foreach t_v* [ eval version=(pow(10, (<<MATCHSTR>>-3) * 3)) * <<FIELD>> + coalesce(version, 0) ]
| eval rounded_value=round(version, 9)
| fields - t_v*
| eventstats max(dv) as max_dv
| eval ComplianceStatus=if(dv = max_dv, "Compliant", "NonCompliant")Note that all this is telling you is that the driver version is the same as the highest one in the file - does that mean compliance to you? What if none are compliant? This does not handle this case.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You have a number of issues:
You driver version is a string, so max() will take the max from a text based point of view, not numeric.
Your stats command will ONLY result in a single field as stats does aggregation so will only leave you the MaxDriverVersion field.
Your statement if (DriverVersion = "MaxDriverVersion" ...) is asking if the DriverVersion field (which does not exist due to stats command) is equal to the string MaxDriverVersion.
You could used 'eventstats...' instead of stats command in which case you would have the DriverVersion field remaining. That would give you part of what you want - but the max issue is still signigicant, e.g.
comparing version 30.0.100.9805 and version 30.0.99.9805.
30.0.99.9805 would be the max() of those two values.