Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How to chart a daily count of HTTP status codes di...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
sourcetype=your_sourcetype earliest=-7d@d | timechart count by status
This search will give the last week's daily status counts in different colors. You'll likely have 200 off the chart so it may be worth making the 200 an overlay. Go to Format > Chart Overlay and select 200, then view it as it's own axis in order to let the other codes actually be seen. I also stacked the values so they're easier to see too.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, what can I do if I wanted to group all the 400 in the same color?
Thanks,
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This question is over two years old with an accepted answer. If you have a similar problem, please post a new question.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
sourcetype=your_sourcetype earliest=-7d@d | timechart count by status
This search will give the last week's daily status counts in different colors. You'll likely have 200 off the chart so it may be worth making the 200 an overlay. Go to Format > Chart Overlay and select 200, then view it as it's own axis in order to let the other codes actually be seen. I also stacked the values so they're easier to see too.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you, i was trying like below, can you please check the below query, how to get the results using bin and span command with chart,
index="nbcutelemundo" | bin span=1s _time | stats count(status) as status_count by _time,status | chart status_count by _time,status span=1d
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
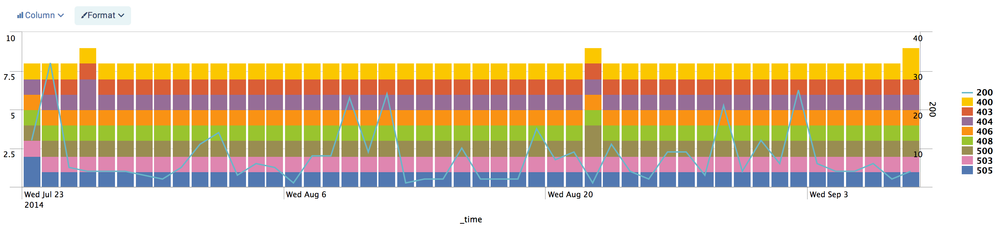
sourcetype=access_combined status=* | bucket _time span=1d | chart count by _time, status
Once again, I overlaid the 200's so that you can actually see the other values.

- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
thank you so much!