- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: How to change color of a Panel based on String
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi All,I am running a dashboard which returns the total count(stats count) of field mentioning Severity=ok or Severity=Critical.
The requirement is if atealst one field value is Severity=Critical, the color of the panel should turn to Red otherwise Green when Severity=Ok.
Can someone please suggest.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
OK Try this
<dashboard version="1.1" theme="dark">
<search id="base_search">
<query>| inputlookup kv_cmdb_as_entity_kpi_lookup WHERE NOT kpi="*~~*" AND host IN (X,Y)
[
search index="itsi_grouped_alerts" kpi=* severity=* entity_name=* earliest=-60m@m
| stats latest(_time) as time latest(severity) as severity by entity_name kpi
| eval host=lower(mvindex(split(entity_name, "."), 0))
| table host kpi severity time
]
| eval severity=coalesce(severity, 2), n=now(), time=coalesce(time, n), time=strftime(time, "%Y-%m-%d %H:%M:%S")
| fields - n _key _timediff
| sort - severity host kpi
| eval severity=case(severity == 2, "OK", severity == 4, "MEDIUM", severity == 6, "CRITICAL")
| fields host kpi severity
| rename host as Host, kpi as KPI, severity as Severity
</query>
<earliest>-24h@h</earliest>
<latest>now</latest>
<sampleRatio>1</sampleRatio>
</search>
<label>Application Dashboard</label>
<row>
<panel depends="$alwaysHide$">
<html>
<style>
#single_prd text {
fill: $single_text_colour$ !important;
}
</style>
</html>
</panel>
<panel>
<title>PRD</title>
<single id="single_prd">
<title>Server Name</title>
<search base="base_search">
<query>| search Host=xyz* Severity=*
| stats count count(eval(Severity=="CRITICAL")) as _critical
| eval _colour=if(_critical>0,"red","green")</query>
<done>
<set token="single_text_colour">$result._colour$</set>
</done>
</search>
<option name="colorBy">value</option>
<option name="colorMode">none</option>
<option name="drilldown">all</option>
<option name="numberPrecision">0</option>
<option name="refresh.display">progressbar</option>
<option name="showSparkline">1</option>
<option name="showTrendIndicator">1</option>
<option name="trellis.enabled">0</option>
<option name="trellis.scales.shared">1</option>
<option name="trellis.size">medium</option>
<option name="trendColorInterpretation">standard</option>
<option name="trendDisplayMode">absolute</option>
<option name="unitPosition">after</option>
<option name="useColors">0</option>
<option name="useThousandSeparators">1</option>
</single>
</panel>
</row>
</dashboard>- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You could use CSS to change the colour of the panel using a token which is set based on the results of the search.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to achieve this ?
My query is index =* Severity=* | stats count
Here Severity can be either "CRITICAL" or "OK"
I want to display red if the Severity is "CRITICAL" or "OK" . (It can be 100 events OK and 50 as CRITICAL.) If all are OK then display GREEN
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Start with this
index =* Severity=* | stats count(eval(Severity=="CRITICAL")) as Critical count(eval(Severity=="OK")) as OK
| eval colour=if(insnotnull(Critical) and Critical > 0, "red", "green")Then in your done handler, set a token to $result.colour$ and use this token in your CSS.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
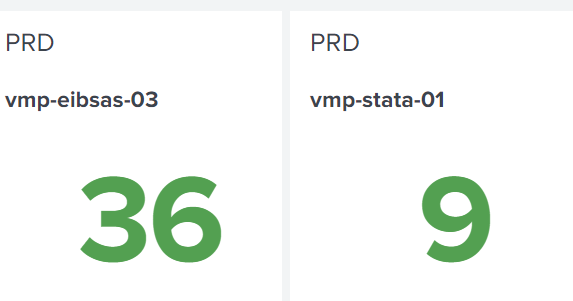
Hi @ITWhisperer Apologies but I don't know using CSS. Will it be possible to provide me the XML.
For example I want to highlight the server vmp-stata-01 as Red as it has one "critical" Severity field and 8 "OK"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please share your dashboard source for this panel in a codeblock
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
<dashboard version="1.1" theme="dark">
<search id="base_search">
<query>| inputlookup kv_cmdb_as_entity_kpi_lookup WHERE NOT kpi="*~~*" AND host IN (X,Y)
[
search index="itsi_grouped_alerts" kpi=* severity=* entity_name=* earliest=-60m@m
| stats latest(_time) as time latest(severity) as severity by entity_name kpi
| eval host=lower(mvindex(split(entity_name, "."), 0))
| table host kpi severity time
]
| eval severity=coalesce(severity, 2), n=now(), time=coalesce(time, n), time=strftime(time, "%Y-%m-%d %H:%M:%S")
| fields - n _key _timediff
| sort - severity host kpi
| eval severity=case(severity == 2, "OK", severity == 4, "MEDIUM", severity == 6, "CRITICAL")
| fields host kpi severity
| rename host as Host, kpi as KPI, severity as Severity
</query>
<earliest>-24h@h</earliest>
<latest>now</latest>
<sampleRatio>1</sampleRatio>
</search>
<label>Application Dashboard</label>
<row>
<panel>
<title>PRD</title>
<single>
<title>Server Name</title>
<search base="base_search">
<query>| search Host=xyz* Severity=*
| stats count</query>
</search>
<option name="colorBy">value</option>
<option name="colorMode">none</option>
<option name="drilldown">all</option>
<option name="numberPrecision">0</option>
<option name="rangeColors">["0x53a051","0x53a051"]</option>
<option name="rangeValues">[0]</option>
<option name="refresh.display">progressbar</option>
<option name="showSparkline">1</option>
<option name="showTrendIndicator">1</option>
<option name="trellis.enabled">0</option>
<option name="trellis.scales.shared">1</option>
<option name="trellis.size">medium</option>
<option name="trendColorInterpretation">standard</option>
<option name="trendDisplayMode">absolute</option>
<option name="unitPosition">after</option>
<option name="useColors">1</option>
<option name="useThousandSeparators">1</option>
</single>
</panel>
</row>
</dashboard>- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@ITWhisperer Appreciate your help on this one.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Try something like this
<dashboard version="1.1" theme="dark">
<search id="base_search">
<query>| inputlookup kv_cmdb_as_entity_kpi_lookup WHERE NOT kpi="*~~*" AND host IN (X,Y)
[
search index="itsi_grouped_alerts" kpi=* severity=* entity_name=* earliest=-60m@m
| stats latest(_time) as time latest(severity) as severity by entity_name kpi
| eval host=lower(mvindex(split(entity_name, "."), 0))
| table host kpi severity time
]
| eval severity=coalesce(severity, 2), n=now(), time=coalesce(time, n), time=strftime(time, "%Y-%m-%d %H:%M:%S")
| fields - n _key _timediff
| sort - severity host kpi
| eval severity=case(severity == 2, "OK", severity == 4, "MEDIUM", severity == 6, "CRITICAL")
| fields host kpi severity
| rename host as Host, kpi as KPI, severity as Severity
</query>
<earliest>-24h@h</earliest>
<latest>now</latest>
<sampleRatio>1</sampleRatio>
</search>
<label>Application Dashboard</label>
<row>
<panel>
<title>PRD</title>
<single>
<title>Server Name</title>
<search base="base_search">
<query>| search Host=xyz* Severity=*
| eval range=if(Severity=="CRITICAL",6,0)
| fields Host KPI range</query>
</search>
<option name="colorBy">value</option>
<option name="colorMode">none</option>
<option name="drilldown">all</option>
<option name="numberPrecision">0</option>
<option name="rangeColors">["0x53a051","0xff0000"]</option>
<option name="rangeValues">[6]</option>
<option name="refresh.display">progressbar</option>
<option name="showSparkline">1</option>
<option name="showTrendIndicator">1</option>
<option name="trellis.enabled">1</option>
<option name="trellis.scales.shared">1</option>
<option name="trellis.size">medium</option>
<option name="trendColorInterpretation">standard</option>
<option name="trendDisplayMode">absolute</option>
<option name="unitPosition">after</option>
<option name="useColors">1</option>
<option name="useThousandSeparators">1</option>
</single>
</panel>
</row>
</dashboard>- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @ITWhisperer I tried but this Sub query but it won't work because I have more than 100 KPI's. Here I am interested only in the count and turn Red/Green if any one of the Severity is triggered.
<query>| search Host=xyz* Severity=* | eval range=if(Severity=="CRITICAL",6,0) | fields Host KPI range</query>
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
OK Try this
<dashboard version="1.1" theme="dark">
<search id="base_search">
<query>| inputlookup kv_cmdb_as_entity_kpi_lookup WHERE NOT kpi="*~~*" AND host IN (X,Y)
[
search index="itsi_grouped_alerts" kpi=* severity=* entity_name=* earliest=-60m@m
| stats latest(_time) as time latest(severity) as severity by entity_name kpi
| eval host=lower(mvindex(split(entity_name, "."), 0))
| table host kpi severity time
]
| eval severity=coalesce(severity, 2), n=now(), time=coalesce(time, n), time=strftime(time, "%Y-%m-%d %H:%M:%S")
| fields - n _key _timediff
| sort - severity host kpi
| eval severity=case(severity == 2, "OK", severity == 4, "MEDIUM", severity == 6, "CRITICAL")
| fields host kpi severity
| rename host as Host, kpi as KPI, severity as Severity
</query>
<earliest>-24h@h</earliest>
<latest>now</latest>
<sampleRatio>1</sampleRatio>
</search>
<label>Application Dashboard</label>
<row>
<panel depends="$alwaysHide$">
<html>
<style>
#single_prd text {
fill: $single_text_colour$ !important;
}
</style>
</html>
</panel>
<panel>
<title>PRD</title>
<single id="single_prd">
<title>Server Name</title>
<search base="base_search">
<query>| search Host=xyz* Severity=*
| stats count count(eval(Severity=="CRITICAL")) as _critical
| eval _colour=if(_critical>0,"red","green")</query>
<done>
<set token="single_text_colour">$result._colour$</set>
</done>
</search>
<option name="colorBy">value</option>
<option name="colorMode">none</option>
<option name="drilldown">all</option>
<option name="numberPrecision">0</option>
<option name="refresh.display">progressbar</option>
<option name="showSparkline">1</option>
<option name="showTrendIndicator">1</option>
<option name="trellis.enabled">0</option>
<option name="trellis.scales.shared">1</option>
<option name="trellis.size">medium</option>
<option name="trendColorInterpretation">standard</option>
<option name="trendDisplayMode">absolute</option>
<option name="unitPosition">after</option>
<option name="useColors">0</option>
<option name="useThousandSeparators">1</option>
</single>
</panel>
</row>
</dashboard>- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @ITWhisperer Wonderful. The solution seems to be working. I have a small modification in requirement.
If the Severity is "Critical" then it should display Red, If "OK" then green , if "Amber" then yellow.
Can you please help me with that.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@ITWhisperer Can you tell me the correct quere based on the case mentioned in my previous reply.
| stats count count(eval(Severity=="CRITICAL")) as _critical | eval _colour=if(_critical>0,"red","green")</query>
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
See my previous response
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I managed to do this with below query. Thanks for all your help
| stats count count(eval(Severity=="CRITICAL")) as _critical count(eval(Severity=="OK")) as _ok count(eval(Severity=="MEDIUM")) as _medium
| eval _colour=case(_critical>0 AND _medium>0,"red","green",_critical=0 AND _medium>0,"yellow","green",_critical=0 AND _medium=0,"green","red")
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It looks like your case function is not set up correctly, although this could just be a copy/paste error?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Indeed it was a typo 🙂
| stats count count(eval(Severity=="CRITICAL")) as _critical count(eval(Severity=="OK")) as _ok count(eval(Severity=="MEDIUM")) as _medium
| eval _colour=case(_critical>0 AND _medium>0,"red",_critical=0 AND _medium>0,"yellow","_critical=0 AND _medium=0,"green")
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
OK now your logic seems a little unrobust. What happens if _critical > 0 and _medium = 0?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@ITWhisperer Thanks for pointing it out as i am new in SPL 😞
Is this alright ?
| eval _colour=case(_critical>0 AND _medium>0,"red",_critical=0 AND _medium>0,"yellow","_critical=0 AND _medium=0,"green",_critical>0 AND _medium=0, "yellow")
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It is not really a SPL issue, it is logic. You tell me - what would be set if _critical is 1 and _medium is 0?
Is this what you want it to be?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@ITWhisperer I am not checking the query before replying 😞
I set it to red now.
| eval _colour=case(_critical>0 AND _medium>0,"red",_critical=0 AND _medium>0,"yellow","_critical=0 AND _medium=0,"green",_critical>0 AND _medium=0, "red")