Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: How do I extract non-blank lines from Windows ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am trying to write a Report which queries our Windows Security Event logs for event # 4738, "user account was changed." There is a field, MSADChangedAttribute, which looks like this:
SAM Account Name: -
Display Name: -
User Principal Name: -
Home Directory: -
Home Drive: -
Script Path: -
Profile Path: -
User Workstations: -
Password Last Set: 1/26/2021 2:31:01 AM
Account Expires: -
Primary Group ID: -
AllowedToDelegateTo: -
Old UAC Value: -
New UAC Value: -
User Account Control: -
User Parameters: -
SID History: -
Logon Hours: -I want to make the Report more condensed and human-readable by extracting only the lines in that field which do not include "-". I have successfully identified the regex command which does this but I can't figure-out how to write it as a rex extract?
For instance, the following code works on regex101.com to extract a new 'output' field
(?<output>^[^-]*$)but when I put that into rex it has no result
| rex field=MSADChangedAttribute max_match=0 "(?<Changed>^[^-]*$)"(NOTE: I added 'max_match=0' because sometimes there are more than 1 lines with new changes)
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
OK, I finally figured it out. I had to make two changes:
- use regex to replace all line-breaks (\r\n) with a delimiter (***)
- convert multi-line "MSADChangedAttributes" into a multi-value field
Now my original regex works!
| rex mode=sed field=MSADChangedAttributes "s/\r\n/***/g"
| makemv delim="***" MSADChangedAttributes
| rex field=MSADChangedAttributes max_match=0 "(?<Changed>^[^-]*$)"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I think maybe the issue here is that Splunk is seeing that 'MSADChangedAttribue' as one long string (albeit with a bunch of line-breaks), i.e., there will always be a "-" character somewhere. Instead, maybe I need to break the original field into multiple fields -- so that the regex can evaluate them individually?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
OK, I finally figured it out. I had to make two changes:
- use regex to replace all line-breaks (\r\n) with a delimiter (***)
- convert multi-line "MSADChangedAttributes" into a multi-value field
Now my original regex works!
| rex mode=sed field=MSADChangedAttributes "s/\r\n/***/g"
| makemv delim="***" MSADChangedAttributes
| rex field=MSADChangedAttributes max_match=0 "(?<Changed>^[^-]*$)"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello ttovarzoll,
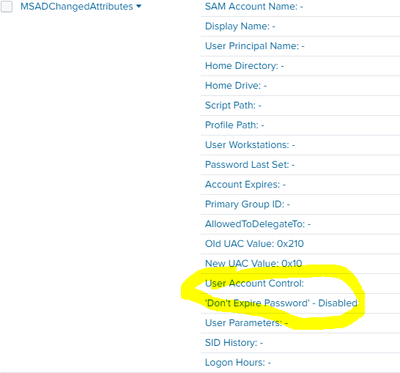
Thank you for providing your solutions. Unfortunately it doesn't work in all cases as showed in the following screenshots where the 'User Account Control' is filled. I can image that this is also the case for other fields.
Did you came across this issue and do you perhaps have an solution for this?
Kind regards,
Jos
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Try something like this on the original (unedited) field
| rex field=MSADChangedAttributes max_match=0 "(?m)(?<Changed>^[^-]*$)"- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Unfortunately that doesn't do the trick, it seems that the regex below used to replace all line-breaks (\r\n) with a delimiter (***) is at fault :
| rex mode=sed field=MSADChangedAttributes "s/\r\n/***/g"
It produces an extra "***' after 'User Account Control:'
So somehow I have to take into account that multiple line-breaks need to be replaced ..
SAM Account Name: -
Display Name: -
User Principal Name: -
Home Directory: -
Home Drive: -
Script Path: -
Profile Path: -
User Workstations: -
Password Last Set: -
Account Expires: -
Primary Group ID: -
AllowedToDelegateTo: -
Old UAC Value: 0x210
New UAC Value: 0x10
User Account Control:
'Don't Expire Password' - Disabled
User Parameters: -
SID History: -
Logon Hours: -
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As I said, use my rex on the unedited field, i.e. replace the three lines in the solution with just my one line.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ah oke, I just did that and also this doesn't work as can me seen at: https://regex101.com/r/Papbq3/1
As to make matters worse, the 'User Account Control' field can contain multiple values when you for example disable an account and at the same time enable the ' Don't Expire Password'. 😓 (https://regex101.com/r/OBVqt2/1)
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please raise a new question detailing your inputs events (examples), expected results and logic used to get the expected results.