Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How do I edit my regular expression to extract a f...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
I am trying to extract a field from a log event, but need help as my RegEx seems to be wrong.
Input string:
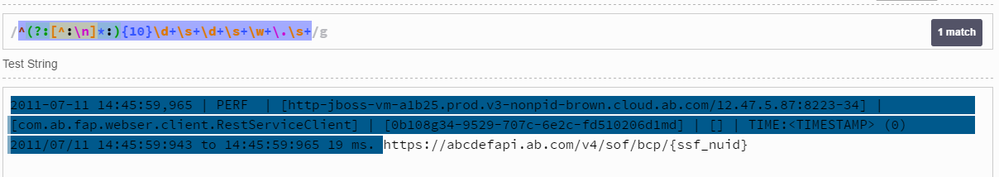
2011-07-11 14:45:59,965 | PERF | [http-jboss-vm-a1b25.prod.v3-nonpid-brown.cloud.ab.com/12.47.5.87:8223-34] | [com.ab.fap.webser.client.RestServiceClient] | [0b108g34-9529-707c-6e2c-fd510206d1md] | [] | TIME: (0) 2011/07/11 14:45:59:943 to 14:45:59:965 19 ms. https://abcdefapi.ab.com/v4/sof/bcp/{ssf_nuid}
Regular expression used: ^(?:[^:\n]*:){10}\d+\s+\d+\s+\w+\.\s+
The regular expression matches the string up to ms as given below,
I want to extract anything after ms i.e. the value "https://abcdefapi.ab.com/v4/sof/bcp/{ssf_nuid}" in this case.
Please tell me what is incorrect in the below command or what the correct command is.
Command used:
source="abc.log"|rex field=_raw "^(?:[^:\n]*:){10}\d+\s+\d+\s+\w+\.\s+(?P)\w+" does not extract
NOTE: All field values have been changed to dummy values and do not represent the real configurations.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You're falling into the common trap of trying to match more than is necessary. If you're only interested in the URL, then write a regex for a URL. This works with your sample.
source="abc.log" | rex "(?<url>http[s]:\/\/.*)" | ...
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you just want to capture everything after ms till the end, you can use this regex
\d+\s+ms\.\s+(?<url>.*)
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You're falling into the common trap of trying to match more than is necessary. If you're only interested in the URL, then write a regex for a URL. This works with your sample.
source="abc.log" | rex "(?<url>http[s]:\/\/.*)" | ...
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
upvote on this, because it matches in less steps and therefore is much faster 😉