Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How do I combine start time from one event and end...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
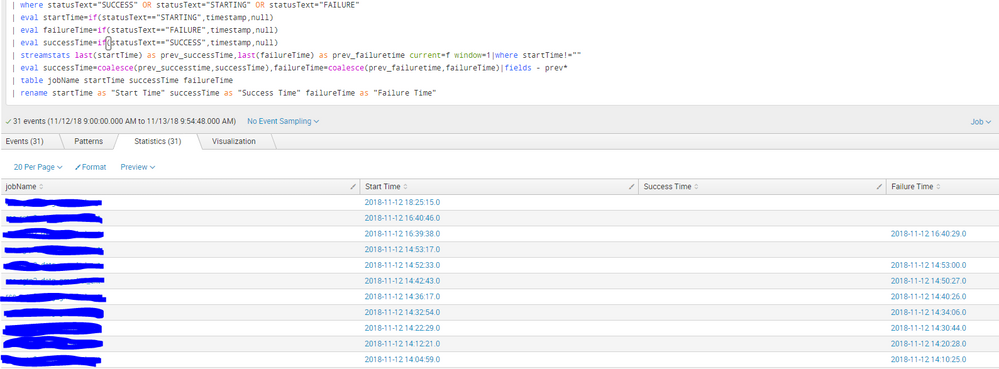
I have the following search that generates the below table. How do i get the starting timestamp and the Success or Failure timestamp in the same row as the starting timestamp when these values are all in separate events (one event has start time of job X, next has success/failure time of job X). They will also need to be associated in the right order.
index=XXX source=XXX jobName=XXX
| where statusText="SUCCESS" or statusText="STARTING" or statusText="FAILURE"
| eval startTime=if(statusText=="STARTING",timestamp,null)
| eval failureTime=if(statusText=="FAILURE",timestamp,null)
| eval successTime=if(statusText=="SUCCESS",timestamp,null)
| table jobName startTime successTime failureTime
| rename startTime as "Start Time" successTime as "Success Time" failureTime as "Failure Time"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@x213217,
Try adding this to your search before the last line in your search (rename)
|streamstats last(successTime) as prev_successTime,last(failureTime) as prev_failuretime current=f window=1|where startTime!=""
|eval successTime=coalesce(prev_successtime,successTime),failureTime=coalesce(prev_failuretime,failureTime)|fields - prev*
Final search
index=XXX source=XXX jobName=XXX
| where statusText="SUCCESS" or statusText="STARTING" or statusText="FAILURE"
| eval startTime=if(statusText=="STARTING",timestamp,null)
| eval failureTime=if(statusText=="FAILURE",timestamp,null)
| eval successTime=if(statusText=="SUCCESS",timestamp,null)
| table jobName startTime successTime failureTime
| streamstats last(startTime) as prev_successTime,last(failureTime) as prev_failuretime current=f window=1|where startTime!=""
| eval successTime=coalesce(prev_successtime,successTime),failureTime=coalesce(prev_failuretime,failureTime)|fields - prev*
| rename startTime as "Start Time" successTime as "Success Time" failureTime as "Failure Time"
What goes around comes around. If it helps, hit it with Karma 🙂
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@x213217,
Try adding this to your search before the last line in your search (rename)
|streamstats last(successTime) as prev_successTime,last(failureTime) as prev_failuretime current=f window=1|where startTime!=""
|eval successTime=coalesce(prev_successtime,successTime),failureTime=coalesce(prev_failuretime,failureTime)|fields - prev*
Final search
index=XXX source=XXX jobName=XXX
| where statusText="SUCCESS" or statusText="STARTING" or statusText="FAILURE"
| eval startTime=if(statusText=="STARTING",timestamp,null)
| eval failureTime=if(statusText=="FAILURE",timestamp,null)
| eval successTime=if(statusText=="SUCCESS",timestamp,null)
| table jobName startTime successTime failureTime
| streamstats last(startTime) as prev_successTime,last(failureTime) as prev_failuretime current=f window=1|where startTime!=""
| eval successTime=coalesce(prev_successtime,successTime),failureTime=coalesce(prev_failuretime,failureTime)|fields - prev*
| rename startTime as "Start Time" successTime as "Success Time" failureTime as "Failure Time"
What goes around comes around. If it helps, hit it with Karma 🙂
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nevermind got it to work! thanks
| where statusText="SUCCESS" OR statusText="STARTING" OR statusText="FAILURE"
| eval startTime=if(statusText=="STARTING",timestamp,null)
| eval failureTime=if(statusText=="FAILURE",timestamp,null)
| eval successTime=if(statusText=="SUCCESS",timestamp,null)
| streamstats last(successTime) as prev_successtime,last(failureTime) as prev_failuretime current=f window=1|where startTime!=""
| eval successTime=coalesce(prev_successtime,successTime),failureTime=coalesce(prev_failuretime,failureTime)|fields - prev*
| table jobName startTime successTime failureTime
| rename startTime as "Start Time" successTime as "Success Time" failureTime as "Failure Time"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello and thank you for your response - I believe this is very close - However it seems to be leaving out the successTime as you can see in the new screenshot i posted above
the startTime seems to match up with the failure time but for events with the SUCCESS timestamp it does not appear in the table? any suggestions on how to fix this ?
thanks.