Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: Field Extraction from Multi line _raw data
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Field Extraction from Multi line _raw data
Hi,
I want to extract the fields Name, Version, VendorName, usesLicensing, LicenseType, ExpiractDateString, LicenseKey, SEN based on delimiter(:) from the below raw data
Could someone please help me with the query for field extraction.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In a single event, I have multiple rows,
(having 7 colons (:) )for each row
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Consider onboarding the data as CSV (Colon-Separated Value) so Splunk handles the field extraction for you.
If you want to do it yourself then this regex should do it.
"(?<name>[^"]+)":"(?<version>[^"]+)":"(?<VendorName>[^"]+)":"(?<usesLicensing>[^"]+)":(?:"(?<LicenseType>[^"]*)")?:(?:"(?<ExpiryDateString>[^"]*)")?:(?:"(?<LicenseKey>[^"]*)")?:(?:"(?<SEN>[^"]*)")?If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This regex is not working,
Could you please help me with the Line_Breaker
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
When that regex is used in the rex command the embedded quotation marks must be escaped, like this:
"(?<name>[^\\\"]+)\\\":\\\"(?<version>[^\\\"]+)\\\":\\\"(?<VendorName>[^\\\"]+)\\\":\\\"(?<usesLicensing>[^\\\"]+)\\\":(?:\\\"(?<LicenseType>[^\\\"]*)\\\")?:(?:\\\"(?<ExpiryDateString>[^\\\"]*)\\\")?:(?:\\\"(?<LicenseKey>[^\\\"]*)\\\")?:(?:\\\"(?<SEN>[^\\\"]*)\\\")?What LINE_BREAKER? This is the first mention of that. Please post a new question about it.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for your response!
The Query which I"m trying is:
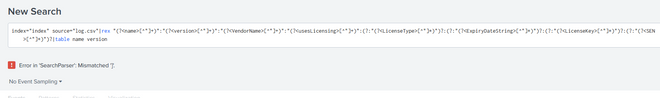
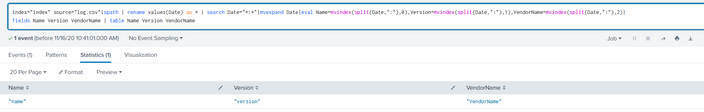
index="index" source="E:\\Logs\\log.csv"|rename values(Date) as * | search Date="*:*"| mvexpand Date|
eval Name=mvindex(split(Date,":"),0), Version=mvindex(split(Date,":"),1), VendorName=mvindex(split(Date,":"),2) |fields Name Version VendorName | table Name Version VendorName
The field names to extract are name, version, VendorName, usesLicensing, LicenseType, ExpiryDateString, LicenseKey, SEN
But I'm to extract only one row from the below Event
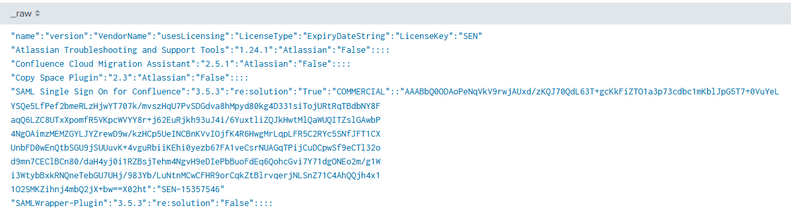
Event Data:(having multiple rows in single event)
"name":"version":"VendorName":"usesLicensing":"LicenseType":"ExpiryDateString":"LicenseKey":"SEN"
"Atlassian Troubleshooting and Support Tools":"1.24.1":"Atlassian":"False"::::
"Confluence Cloud Migration Assistant":"2.5.1":"Atlassian":"False"::::
"Copy Space Plugin":"2.3":"Atlassian":"False"::::
"SAML Single Sign On for Confluence":"3.5.3":"re:solution":"True":"COMMERCIAL"::"AAABbQ0ODAoPeNqVkV9rwjAUxd/zKQJ70QdL63T+gcKkFiZTO1a3p73cdbc1mKblJpG5T7+0VuYeL
YSQe5LfPef2bmeRLzHjwYT707k/mvszHqU7PvSDGdva8hMpyd80kg4D331siTojURtRqTBdbNY8F
aqQ6LZC8UTxXpomfR5VKpcWVYY8r+j62EuRjkh93uJ4i/6YuxtliZQJkHwtMlQaWUQITZslGAwbP
4NgOAimzMEMZGYLJYZrewD9w/kzHCp5UeINCBnKVvIOjfK4R6HwgMrLqpLFR5C2RYc5SNfJFT1CX
UnbFD0wEnQtbSGU9jSUUuvK+4vguRbiiKEhi0yezb67FA1veCsrNUAGqTPijCuDCpwSf9eCTl32o
d9mn7CEClBCn80/daH4yj0i1RZBsjTehm4NgvH9eDIePbBuoFdEq6QohcGvi7Y71dgONEo2m/g1W
i3WtybBxkRNQneTebGU7UHj/983Yb/LuNtnMCwCFHR9orCqkZtBlrvqerjNLSnZ71C4AhQQjh4x1
1O2SMKZihnj4mbQ2jX+bw==X02ht":"SEN-15357546"
"SAMLWrapper-Plugin":"3.5.3":"re:solution":"False"::::
"Team Calendars":"6.0.49":"Atlassian Pty Ltd":"True":"COMMERCIAL"::"AAABTg0ODAoPeNpdkF9LwzAUxd/zKQK+6MNGWwZdBwGlKzjcH3HVJ0Gu2a0LTdNykwz105t2FXSBv
Nyc/O4556r0yJcoeZzyaL6IZoso4/m+5EkUZ2yJVpLqnGqNKBEanoNGcwCyvGqJ562ptEcjkV/vk
U5INzyOwuHPFsm+LoKiaZCkAs3XSqKxyLa+eUfaVYNEDHLmAvtN/rKnaBxSR8qicOSR5YTQe1iCQ
9Ebm8TJJJ6zsN+BdFtoUKx9Dfab8weoW30JDCJ1GmEXT3sHFLaJCnQwNxKLDSgt9ICc1j3x9ojKY
I1mKtuGFSfQfrA0/tPncC8hUj9MWACEEAZCN8Vnp+hr9J5Eg/f00sbYTvnV4RAn3202xVO+uluzH
X2AUfa87n60wVd9R2YYgmb7YivCnczTLEtmMzbi/qz2RqtGOTywR0/yCBb/t5myH9wCtHUwLgIVA
I9H5o1K8FkD5GzwxpwvJeR1NEfQAhUAkR4yfmoZx9KvHtEXWsZQ8+8qaAM=X02gk":"SEN-8799244"
"techradar":"1.1":"it-economics GmbH":"False"::::
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What have you tried so far?
It would help if you posted the sample event as text rather than a screenshot so we can test without having to re-type that hideous mess (no way I'm typing all of that).
Is the number of fields constant? How about the number of ":"s? We need something to key off of to find the values.
If this reply helps you, Karma would be appreciated.