Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: Extraction using rex
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Extraction using rex
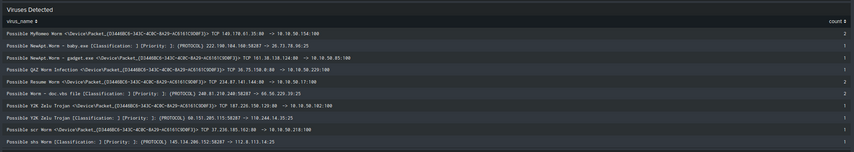
This is a dashboard panel that i've created by extracting virus information from a log file
This is my search query
I actually want to see only the virus names and the IP addresses. So, it should look like this:
How would I change my regex to obtain this result?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is my sample data in text format:
Apr 23 14:13:35 [143.5.113.3] snort[1976]: [1:729:1] Virus - Possible scr Worm <\Device\Packet_{D3446BC6-343C-4C0C-8A29-AC6161C9D0F3}> TCP 37.236.185.162:80 -> 10.10.50.218:100
Apr 23 14:13:35 [143.5.113.3] snort[1976]: [1:779:1] Virus - Possible NewApt.Worm - gadget.exe <\Device\Packet_{D3446BC6-343C-4C0C-8A29-AC6161C9D0F3}> TCP 161.38.138.124:80 -> 10.10.50.85:100
Apr 23 14:13:35 [143.5.113.3] snort[1976]: [1:757:1] Virus - Possible Y2K Zelu Trojan <\Device\Packet_{D3446BC6-343C-4C0C-8A29-AC6161C9D0F3}> TCP 187.226.150.129:80 -> 10.10.50.102:100
Apr 23 14:13:35 [143.5.113.3] snort: [1:767:1] Virus - Possible NewApt.Worm - baby.exe [Classification: ] [Priority: ]: {PROTOCOL} 222.190.104.160:58287 -> 26.73.78.96:25
Apr 23 14:13:35 [143.5.113.3] snort[1976]: [1:727:1] Virus - Possible MyRomeo Worm <\Device\Packet_{D3446BC6-343C-4C0C-8A29-AC6161C9D0F3}> TCP 149.170.61.35:80 -> 10.10.50.154:100
Apr 23 14:13:35 [143.5.113.3] snort[1976]: [1:800:1] Virus - Possible Resume Worm <\Device\Packet_{D3446BC6-343C-4C0C-8A29-AC6161C9D0F3}> TCP 234.87.141.144:80 -> 10.10.50.17:100
Apr 23 14:13:35 [143.5.113.3] snort: [1:801:1] Virus - Possible Worm - doc.vbs file [Classification: ] [Priority: ]: {PROTOCOL} 240.81.210.240:58287 -> 66.56.229.39:25
Apr 23 14:13:35 [143.5.113.3] snort: [1:757:1] Virus - Possible Y2K Zelu Trojan [Classification: ] [Priority: ]: {PROTOCOL} 60.151.205.115:58287 -> 110.244.14.35:25
Apr 23 14:13:50 [143.5.113.3] snort: [1:2266:1] VIRUS OUTBOUND .doc file attachment [Classification: ] [Priority: ]: {PROTOCOL} 234.182.233.181:58287 -> 0.235.220.175:25
Apr 23 14:13:39 [143.5.113.3] snort[1976]: [1:1234:1] WEB-MISC VirusWall FtpSaveCSP access <\Device\Packet_{D3446BC6-343C-4C0C-8A29-AC6161C9D0F3}> TCP 192.69.129.252:80 -> 10.10.50.30:100
Apr 23 14:13:35 [143.5.113.3] snort: [1:730:1] Virus - Possible shs Worm [Classification: ] [Priority: ]: {PROTOCOL} 145.134.206.152:58287 -> 112.8.113.14:25
Apr 23 14:13:35 [143.5.113.3] snort[1976]: [1:732:1] Virus - Possible QAZ Worm Infection <\Device\Packet_{D3446BC6-343C-4C0C-8A29-AC6161C9D0F3}> TCP 36.75.150.0:80 -> 10.10.50.229:100
I only want to retrieve the virus names and IP addresses which are highlighted in red.
And this is my search query in text format:
source="General-linux-sql.log" sourcetype="Linux"
|rex field=_raw "Virus\s-\s(?<virus_name>.*)"
| table virus_name
| stats count by virus_name
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the sample data. This rex command isn't perfect, but should get you close to want you seek.
| rex "snort(?:\[[^\]]+])?: \[[^\]]+] (?<virus>[^\[\<]+).+(?:\{PROTOCOL}|TCP) (?<ip>.*)"If this reply helps you, Karma would be appreciated.