Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: Earliest Time not showing the correct results
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi All, I am confused as in why earliest time modifier is not working out in my case ? Someone pls clarify why is splunk displaying the results this way ?
Below is my search
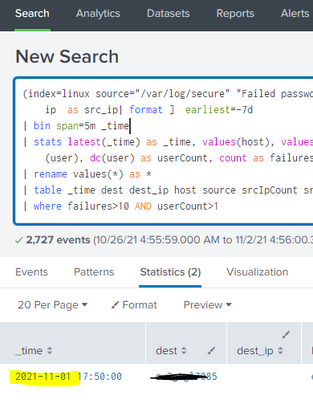
(index=linux source="/var/log/secure" "Failed password") earliest=-1d
| stats latest(_time) as _time, values(host), values(dest_ip), values(source), values(src_ip), values(src), dc(src_ip) as srcIpCount, dc(src) as srcCount, values(user), dc(user) as userCount, count as failures by src_ip dest
| rename values(*) as *
| table _time dest dest_ip host source srcIpCount src_ip srcCount src userCount user failures
| where failures>10 AND userCount>1
This does not show any results with earliest = -1d ( Today being Nov 2 2021)
Now if i change earliest=-7d , then it shows results where _time = Nov 1 2021 which is yesterday. Below screenshot. Why didn't earliest = -1d or even -2d show these results ? What is making -7d pick these up but not -1d or -2d ?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You only get results when (according to your where clause) you have accumulated more than 10 failures and more than 1 user within your time period i.e. there aren't sufficient failures and users until you expand the timeframe to 7 days.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You only get results when (according to your where clause) you have accumulated more than 10 failures and more than 1 user within your time period i.e. there aren't sufficient failures and users until you expand the timeframe to 7 days.