- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- EVAL causes a field to be blank
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
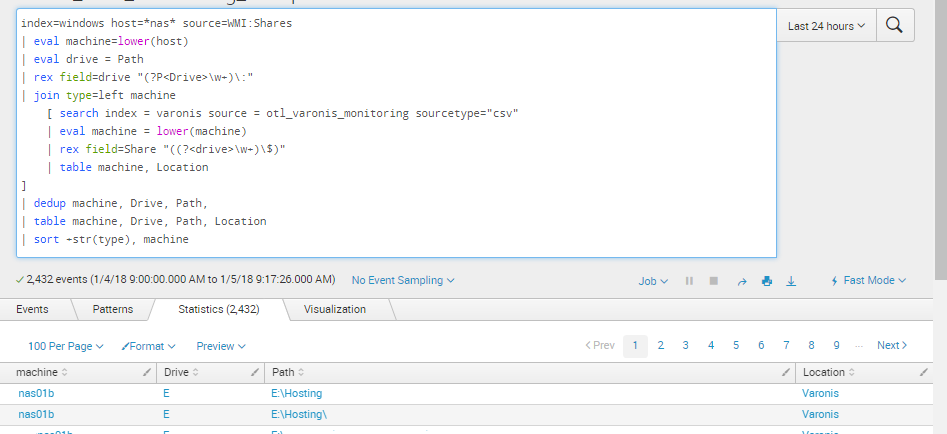
I need the field "Location" added to my search as seen in the screenshot attached. However, in this query below the Location field does not pull through and I have identified that it does work when the | stats values(con_UL) as con_UL by machine line is excluded.
Query below:
index=windows host=*nas* source=WMI:Shares
| eval machine=lower(host)
| eval drive = Path
| rex field=drive "(?P<Drive>\w+)\:"
| eval con_splunk=machine. "," .Drive
| eval con_splunkUL = upper(con_splunk)
| join type=left machine
[ search index = varonis source = otl_varonis_monitoring sourcetype="csv"
| eval machine = lower(machine)
| rex field=Share "((?<drive>\w+)\$)"
| eval con=machine. "," .drive
| eval con_UL = upper(con)
| table machine, Location
| stats values(con_UL) as con_UL by machine ]
| eval MonitoringStatus = if(like(upper(con_UL),"%".upper(con_splunkUL)."%"), "Monitored", "Not Monitored")
| eval Action=if ((MonitoringStatus="Not Monitored")AND(like(Path,"%Hosting%")),"Action Required","No Action Required")
| dedup machine, Drive, Path, MonitoringStatus
| table machine, Drive, Path, MonitoringStatus, Action, Location
| sort +str(type), machine
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi davidcraven02,
after a stats command you have only the fields of your stats (in your example con_UL and machine), so add to your stats command the value of Location
...
| stats values(con_UL) as con_UL values(Location) AS Location by machine
...
Bye.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @davidcraven02,
| stats values(con_UL) as con_UL by machine search part will remove Location field from the search result that's Y it is working if you remove it.
Can you please replace search part and try again ?
SEARCH PART : | stats values(con_UL) as con_UL by machine
NEW : | stats values(con_UL) as con_UL values(Location) as Location by machine
OR | stats values(con_UL) as con_UL by machine,Location
Thanks
Kamlesh
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi davidcraven02,
after a stats command you have only the fields of your stats (in your example con_UL and machine), so add to your stats command the value of Location
...
| stats values(con_UL) as con_UL values(Location) AS Location by machine
...
Bye.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Brilliant man. Spent all day yesterday trying to get this to work.