Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: Dispositions values in reports
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
I am trying to make report which will display what notables were closed with what disposition. But unfortunately when I make report, it shows me values as follows: "disposition:1", "disposition:2" and so on and I cant figure out how to change these values in the way that in chart/graph it will show "false positive" or "true positive".
I found out a way to change name of column (rename as) but I cant find a way to change values itself and if I try to use same logic (rename disposition:1 as false positive) it doesnt make the trick.
Could you point me in the correct direction, please?
Thanks in advance
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Try something like this (obviously expand the case function to cover the other renames)
|`incident_review` | stats count by disposition
| eval disposition=case(disposition=="disposition:1","true-positive",disposition=="disposition:2","false-positive",true(),disposition)- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, this is exactly what I need! I tried to play with eval also, but without that case function. Thank you for your help, much appreciated!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
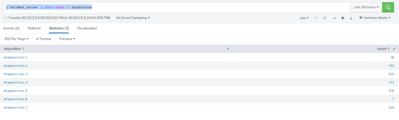
I am using very simple query:
|`incident_review` | stats count by dispositionI get table like this:
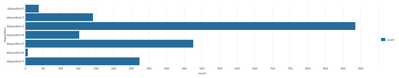
When I make bar chart it looks like this:
What I am trying to do is same bar chart, but instead of disposition:1, disposition:2..., I would like to see there values of these dispositions so for example true-positive, false-positive...
I tried to use "rename as" like this, but it doesnt work - output is same bar chart as above
|`incident_review` | stats count by disposition | rename disposition:1 as true-positive
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Try something like this (obviously expand the case function to cover the other renames)
|`incident_review` | stats count by disposition
| eval disposition=case(disposition=="disposition:1","true-positive",disposition=="disposition:2","false-positive",true(),disposition)- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please provide more information e.g. some sample events (anonymised of course) and your current search, and output, and your expected results.