Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: Create an eval if when the results from stats ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Create an eval if when the results from stats are 0
Is there a way, besides fillnull, to do an eval if(averageResponse=0, 0.000)?
Basically, I want to be able to have the stats table show a result of 0.000 for a field if the results after the stats field is 0 without using a fillnull field in the case where every defined field is equalling zero.
This is the base search:
| datamodel metric summariesonly=true search
| search "metric.date"=2021-06-11 | rename "metric.date" as date
| rename "metric.uri_path" as uri_path
| eval category=case(like(uri_path, "/as/%/resume/as/authorization.ping"), "highPriority", uri_path="/pf/heartbeat.ping", "unattended",
uri_path="/?REF=undefined", "lowPriority", uri_path="/header-logo.svg", "largePayload")
| rename "metric.response_time" as response_time
| stats avg(response_time) by category
| rename avg(response_time) as averageResponse
| eval averageResponse=round(averageResponse,3)
| transpose 0 header_field=category
| fillnull value=0.000 highPriority, lowPriority, largePayload, unattended
| eval _time="$date$"
| fields highPriority, lowPriority, largePayload, unattended, _time
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@ebs wrote:Is there a way, besides fillnull, to do an eval if(averageResponse=0, 0.000)?
Basically, I want to be able to have the stats table show a result of 0.000 for a field if the results after the stats field is 0 without using a fillnull field in the case where every defined field is equalling zero.
It is not clear what is your expected outcome. If all fields equal zero, do you want the stats table to show all 0.0000, or not show all 0.0000?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have a screen shot of what the stats field looks like in my post previous. I would want under every field it to say 0.000 if there are no results
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
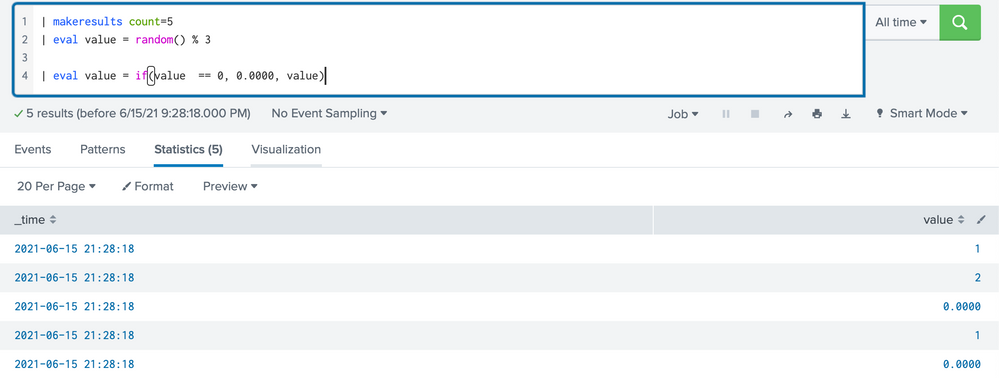
Maybe one more clarification: This exercise is to transform any single digit "0" into a 5-digit decimal "0.0000", as opposed to insert "0.0000" where a value is absent (which is the use case for fillnull). If this is correct, your question is already the answer. I don't see why you cannot use it.
As an example, I use this to generate a sequence of digits between 0 and 2, then transform "0" into "0.0000" using the exact expression in your question:
| makeresults count=5
| eval value = random() % 3
| eval value = if(value == 0, "0.0000", value)
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm finding it overwrites fields with values as well, I only want the if statement to apply to fields where the value is 0
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Fixed that, my issue. But now it won't produce the stats table anyway when there are no results at all
Search:
| datamodel metric summariesonly=true search
| search "metric.date"=2021-06-11
| rename "metric.date" as date
| rename "metric.uri_path" as uri_path
| eval category=case(like(uri_path, "/url1"), "highPriority", uri_path="/url2", "unattended",
uri_path="/url3", "lowPriority", uri_path="/url4", "largePayload")
| rename "metric.response_time" as response_time
| stats avg(response_time) by category
| rename avg(response_time) as averageResponse
| eval averageResponse = if(averageResponse == 0, "0.000", averageResponse)
| eval averageResponse=round(averageResponse,3)
| transpose 0 header_field=category
| fillnull value=0.000 highPriority, lowPriority, largePayload, unattended
| eval _time="$date$"
| fields highPriority, lowPriority, largePayload, unattended, _time
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@ebs wrote:Fixed that, my issue. But now it won't produce the stats table anyway when there are no results at all
To make certain of the situation: A previous search made some false zeros (0); now that you fixed the search, those results become absent (null). As a consequence, the stats table won't show results. Is this correct?
If that is the case (which differs from the title statement), handling all nulls in a timeseries is a common annoyance. I had asked for help several times before, and there have been several recent posts about this. The most recent, and a rather efficient one, is offered by @bowesmana in https://community.splunk.com/t5/Splunk-Search/Need-to-generate-0-results-in-case-of-no-data-availabl...
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So basically the initial eval function I did was overriding the fields with previous values, the ones that were already null were getting filled in by the fillnull which is fine in this moment. But when all of the fields were zero, no stats table would show at all. Just a no results found
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Works if I use your eval with the fillnull, thanks!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
My main issue is when there are no results there is not stats table, that's why I'm looking into doing an eval if statement