Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Splunk Search
×
Join the Conversation
Without signing in, you're just watching from the sidelines. Sign in or Register to connect, share, and be part of the Splunk Community.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: Count occurrences of string and put them in ta...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Vivekmishra01
Explorer
01-10-2023
07:14 AM
I am trying to find few strings in my search query and count occurrences of them and I want to put them in a two column table. I am able to do it with stat command, but it's coming like string as column name and count in the row bwlow. Below is what I am using and what I ma getting.
index=<index> <search String > "Failed" | stats count AS Failed count(eval(searchmatch("Failed Acknowledged"))) AS "Failed Acknowledged" count(eval(searchmatch("UnexpectedException Caught"))) AS "UnexpectedException Caught" count(eval(searchmatch("NonRetryableException Caught"))) AS "NonRetryableException Caught"
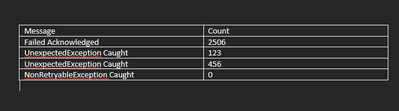
However I want a result like below.
Can anyone help? Thanks in advance.
1 Solution
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
GaetanVP
Contributor
01-10-2023
07:46 AM
Hello !
You could try this :
<your search> | transpose 0 column_name="Message" | rename "row 1" as Count
Good luck!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
FelixLeh
Contributor
01-10-2023
08:15 AM
Hi!
Is this accomplishing what you are looking for? (I assume you are working with untransformed Events here)
index=<index> <search String > "Failed"
| eval Message = case(like(_raw,"%Failed Acknowledged%"),"Failed Acknowledged",like(_raw,"%UnexpectedException Caught%"),"UnexpectedException Caught",like(_raw,"%NonRetryableException Caught%"),"NonRetryableException Caught",true(),NULL)
| stats count by Message
If you want to add a line that sums up the total amount of events you can add the following:
| addtotals fieldname=count col=t labelfield=Message
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
GaetanVP
Contributor
01-10-2023
07:46 AM
Hello !
You could try this :
<your search> | transpose 0 column_name="Message" | rename "row 1" as Count
Good luck!
Get Updates on the Splunk Community!
[Puzzles] Solve, Learn, Repeat: Dynamic formatting from XML events
This challenge was first posted on Slack #puzzles channelFor a previous puzzle, I needed a set of fixed-length ...
Enter the Agentic Era with Splunk AI Assistant for SPL 1.4
🚀 Your data just got a serious AI upgrade — are you ready?
Say hello to the Agentic Era with the ...
Stronger Security with Federated Search for S3, GCP SQL & Australian Threat ...
Splunk Lantern is a Splunk customer success center that provides advice from Splunk experts on valuable data ...