Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Can tables be used with top to display additional...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
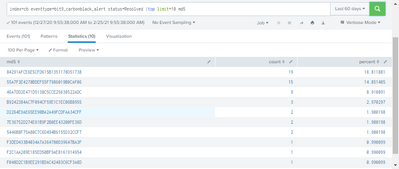
Goal is to return a table that displays the Top 10 (md5) hashes in recorded alerts received over a 60 days period.
So base search is :
index=cb eventtype=bit9_carbonblack_alert status=Resolved|top limit=10 md5
but for each returned result, id like to also show its filename and process_name
index=cb eventtype=bit9_carbonblack_alert status=Resolved |table md5 process_name observed_filename
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @kelie,
Your final query is not much different than mine, since you do not use UID it is better to remove it as an optimization. Below should give the same result;
index=cb eventtype=bit9_carbonblack_alert status=Resolved
| stats values(process_name) as Process values(observed_filename) as Filename count as Hits BY md5
| sort 10 -Hits
| rename md5 as "MD5 Hash"- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @kelie,
Your final query is not much different than mine, since you do not use UID it is better to remove it as an optimization. Below should give the same result;
index=cb eventtype=bit9_carbonblack_alert status=Resolved
| stats values(process_name) as Process values(observed_filename) as Filename count as Hits BY md5
| sort 10 -Hits
| rename md5 as "MD5 Hash"- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
with some tweaking i produced this
index=cb eventtype=bit9_carbonblack_alert status=Resolved
|stats dc(unique_id) as UID count values(process_name) as Process values(observed_filename) as Filename BY md5 |sort 10 -count|fields md5 Process Filename count |rename md5 as "MD5 Hash" count as "Hits"im still new to splunk so critique as needed if not optimized. This query though does line up with the fields i needed and seems to align with a base + top limit search
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
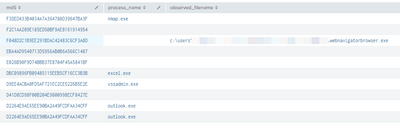
my base search with a top limit yields very different results see below
vs
index=cb eventtype=bit9_carbonblack_alert status=Resolved
| sort 10 - md5
| table md5 process_name observed_filenamevs
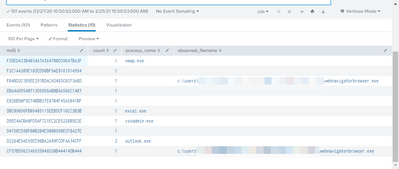
index=cb eventtype=bit9_carbonblack_alert status=Resolved
|stats count values(process_name) as process_name values(observed_filename) as observed_filename by md5
| sort 10 - md5
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Missing process_name or observed_filename fields does not effect the stats since they are not in group by side. They will be listed if any.
That search will show top 10 count for md5 field and available extra fields if any.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @kelie,
You can try with stats to see the details of hashes;
index=cb eventtype=bit9_carbonblack_alert status=Resolved
|stats count values(process_name) as process_name values(observed_filename) as observed_filename by md5
| sort 10 - md5 - Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
index=cb eventtype=bit9_carbonblack_alert status=Resolved
|stats count values(process_name) as process_name values(observed_filename) as observed_filename by md5
| sort 10 - md5 I wouldnt be able to rely on the above as the events do not always have a process_name or observed_name.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The top command discards all fields except the ones in its arguments. Try using sort, instead.
index=cb eventtype=bit9_carbonblack_alert status=Resolved
| sort 10 - md5
| table md5 process_name observed_filenameIf this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
i have to include a top or even a count as i need the top 10 number of events by md5. the additional fields provide context for what the software is
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The sort 10 command is the same as top 10, but doesn't throw away fields. Try it.
If this reply helps you, Karma would be appreciated.