Are you a member of the Splunk Community?
- Find Answers
- :
- Splunk Platform
- :
- Splunk Enterprise
- :
- Re: how do I unquarantine a indexer
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I've recently had to take an indexer offline while I worked on storage so I ended up putting it into quarantine until things were resolved. Now that things are resolved, I can't seem the indexer is receive data but I still have the below error within the monitoring console:
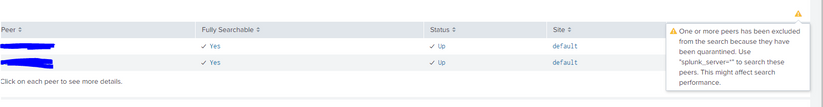
"One or more peers has been excluded from the search because they have been quarantined. Use "splunk_server=*" to search these peers. This might affect search performance."
My cluster manager now sees both indexers (01 and 02) in this group but the there are still errors suggesting the 02 indexer is still quarantined. The indexer02 was the one quarantined which is now receiving data and shows up in the monitoring console but with the above error
Any advice on how to unquarantine this indexer or resolve this message?
I've tried to fiddle around with this DOC but I can't seem to find the correct syntax for the indexer
https://docs.splunk.com/Documentation/Splunk/8.0.6/DistSearch/Quarantineasearchpeer
Thanks,
Sean
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I had to remove the entries in the $SPLUNK_HOME/etc/system/local/distsearch.conf within the master server and restarted. I then went into the monitoring console -> Settings -> enabled the indexer -> corrected the roll to only-indexer -> applied changes. Now the monitoring console looks good.
[distributedSearch]
disabled = 0
disabled_servers = https://<server01>:8089 <---- Removed this
quarantined_servers = https://<server01>:8089 <---- Removed this
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I had to remove the entries in the $SPLUNK_HOME/etc/system/local/distsearch.conf within the master server and restarted. I then went into the monitoring console -> Settings -> enabled the indexer -> corrected the roll to only-indexer -> applied changes. Now the monitoring console looks good.
[distributedSearch]
disabled = 0
disabled_servers = https://<server01>:8089 <---- Removed this
quarantined_servers = https://<server01>:8089 <---- Removed this
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
r. Ismo
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for the reply. This settings area was blank but I ended up having to manually adjust the distsearch.conf file within the master server to remove the server from quarantine.