Are you a member of the Splunk Community?
- Find Answers
- :
- Splunk Platform
- :
- Splunk Enterprise
- :
- Re: No results found in the ADChanges
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
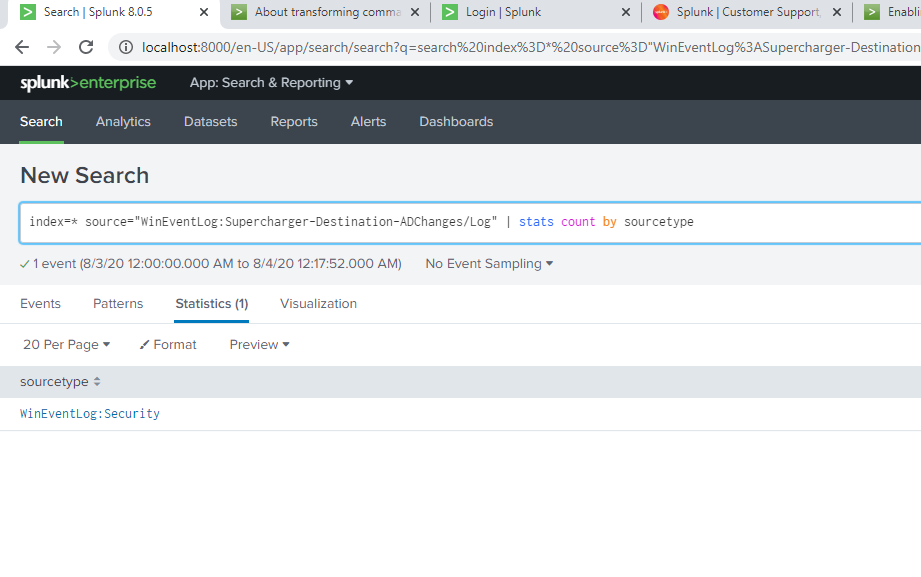
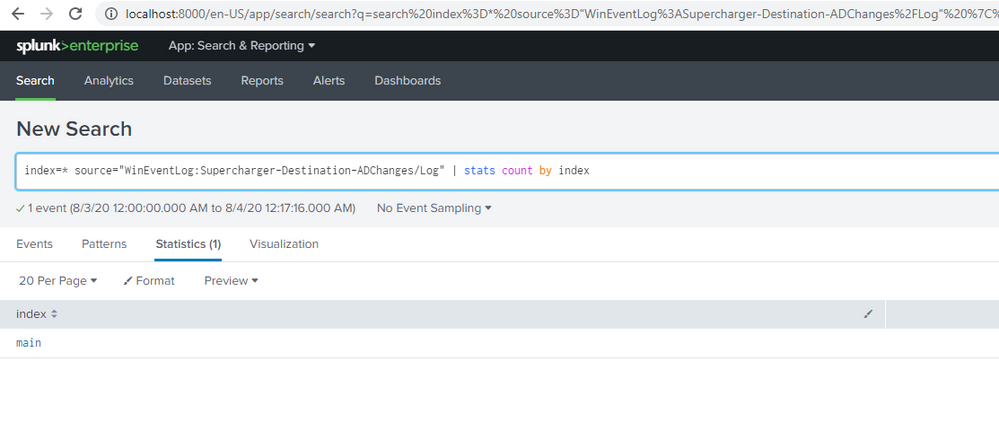
I need to create an audit for AD changes and have followed all steps in https://support.logbinder.com/SuperchargerKB/50135/8-Install-Supercharger-with-Splunk-Light-and-the-Splunk-App-for-LOGbinder . Logs are all showing when I search index=main but no results found in the dashboard and Logbinder for splunk AD changes. I followed some searches from the past threads. Please see attached results. Kindly assist on this. Thank you.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello, Rich.
I think it is solved now. Changed select_winseclog_events definition to index=main. Thank you for your support.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If that dashboard uses the searches shown in the previous screen shots, then the problem may be the errors in the third and fourth searches. Once you resolve those errors the dashboard may show data.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
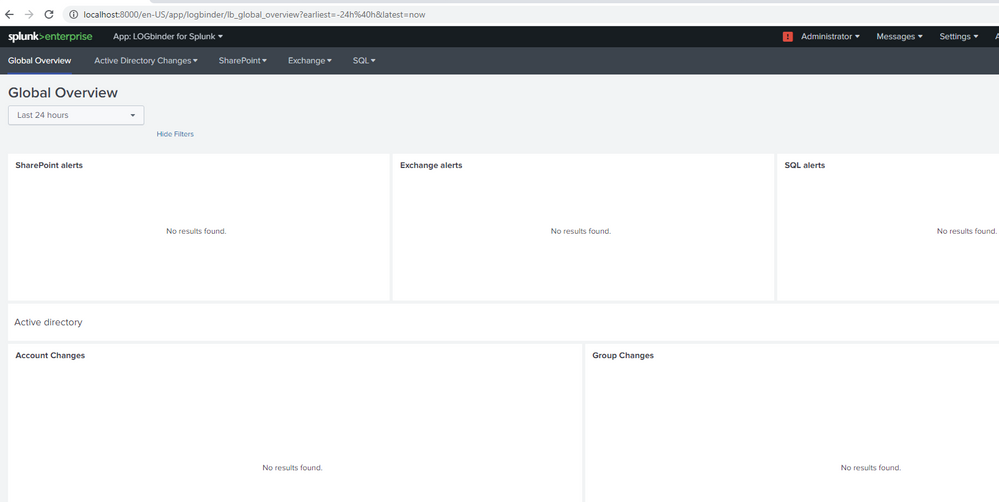
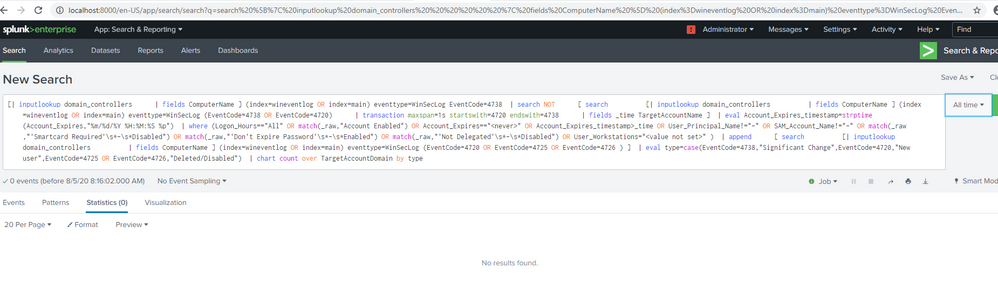
Thank you for your reply. No results found for all filters in the dashboard. For example, under AD changes account changes by domain:
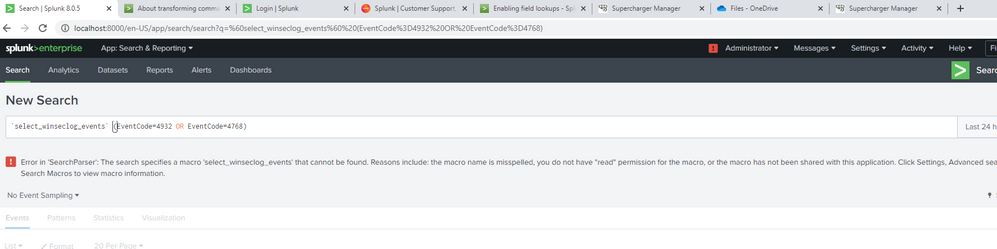
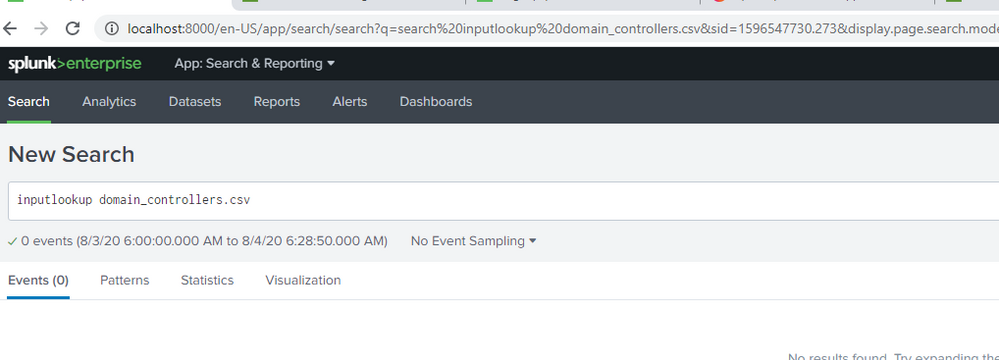
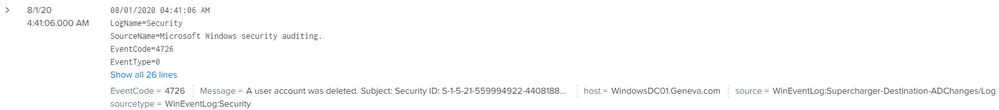
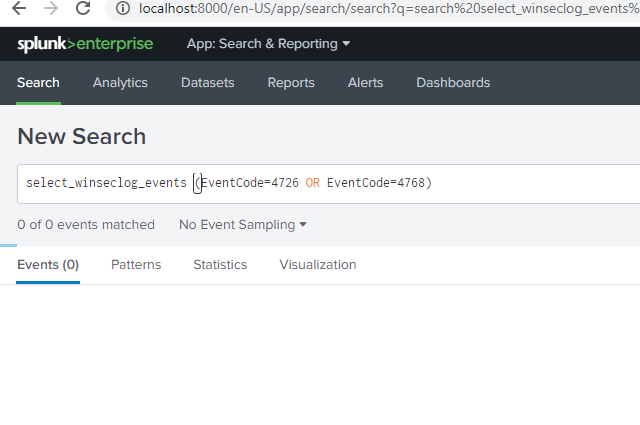
search [ | inputlookup domain_controllers | fields ComputerName ] (index=wineventlog OR index=main) eventtype=WinSecLog EventCode=4738 | search NOT [ search [ | inputlookup domain_controllers | fields ComputerName ] (index=wineventlog OR index=main) eventtype=WinSecLog (EventCode=4738 OR EventCode=4720) |transaction maxspan=1s startswith=4720 endswith=4738 | fields _time TargetAccountName ] | eval Account_Expires_timestamp=strptime(Account_Expires,"%m/%d/%Y %H:%M:%S %p") | where (Logon_Hours=="All" OR match(_raw,"Account Enabled") OR Account_Expires=="<never>" OR Account_Expires_timestamp>_time OR User_Principal_Name!="-" OR SAM_Account_Name!="-" OR match(_raw,"'Smartcard Required'\s*-\s*Disabled") OR match(_raw,"'Don't Expire Password'\s*-\s*Enabled") OR match(_raw,"'Not Delegated'\s*-\s*Disabled") OR User_Workstations="<value not set>" ) | append [search [ | inputlookup domain_controllers | fields ComputerName ] (index=wineventlog OR index=main) eventtype=WinSecLog (EventCode=4720 OR EventCode=4725 OR EventCode=4726 ) ] | eval type=case(EventCode=4738,"Significant Change",EventCode=4720,"New user",EventCode=4725 OR EventCode=4726,"Deleted/Disabled")I found some of the event codes like 4726 in main=index logs so there should be something reflected in the dashboard. How do I solve error: Error in 'SearchParser': The search specifies a macro 'select_winseclog_events' that cannot be found. Reasons include: the macro name is misspelled, you do not have "read" permission for the macro, or the macro has not been shared with this application. Click Settings, Advanced search, Search Macros to view macro information. . when I search for `select_winseclog_events` (EventCode=4932 OR EventCode=4768)?
The fourth image is now resolved when I removed the "|". Please help.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The search specifies a macro 'select_winseclog_events' that cannot be found. Reasons include: the macro name is misspelled, you do not have "read" permission for the macro, or the macro has not been shared with this application. Click Settings, Advanced search, Search Macros to view macro information.The error seems pretty clear about the cause of the error and how to resolve it:
- Make sure you have the right macro name
- Make sure you have permission to read the macro
- Make sure the macro is shared so you can access it
If you obtained the search from an on-line search, you may need to install an app that defines the macro.
inputlookup is a generating command so it must be preceded by a pipe.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello.
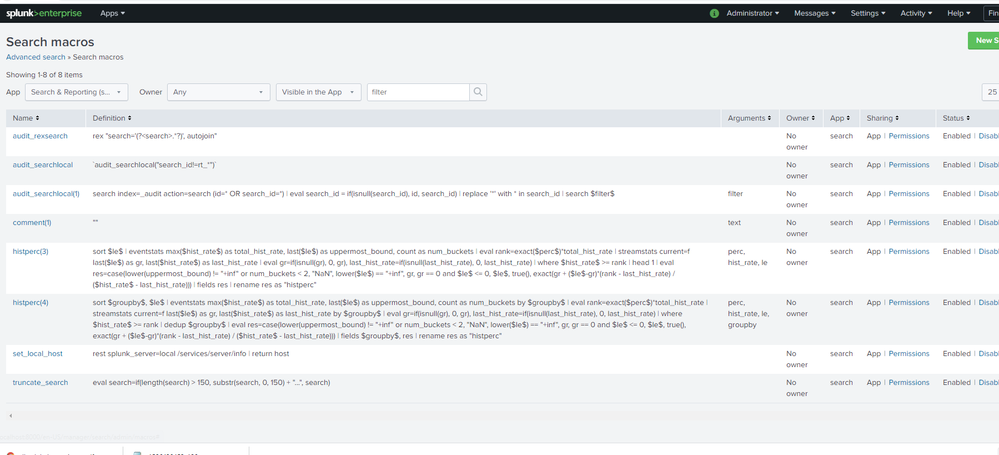
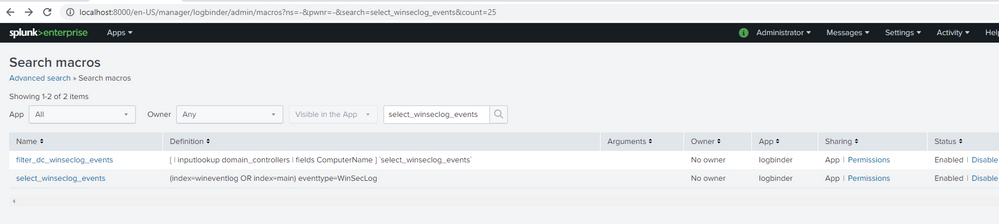
These are my macros. Do I need this `select_winseclog_events` macros to reflect data to the dashboard? Can you please help me how can I add this please? I was not able to find app that defines the macro. Thank you.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If your search uses a macro then you must have a definition for that macro. Where did you get the search if the macro did not come with it?
The screen shot shows only those macros visible to the Search & Reporting app. We already know the macro is not on that list because of the error message. Select "All" from the App menu to see all macros. If the one you're using still isn't on the list then you'll have to create one.
The first Google hit for 'select_winseclog_events' turned up this definition, which may be suitable for you.
[select_winseclog_events]
definition = (index=wineventlog OR index=main) eventtype=WinSecLog
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
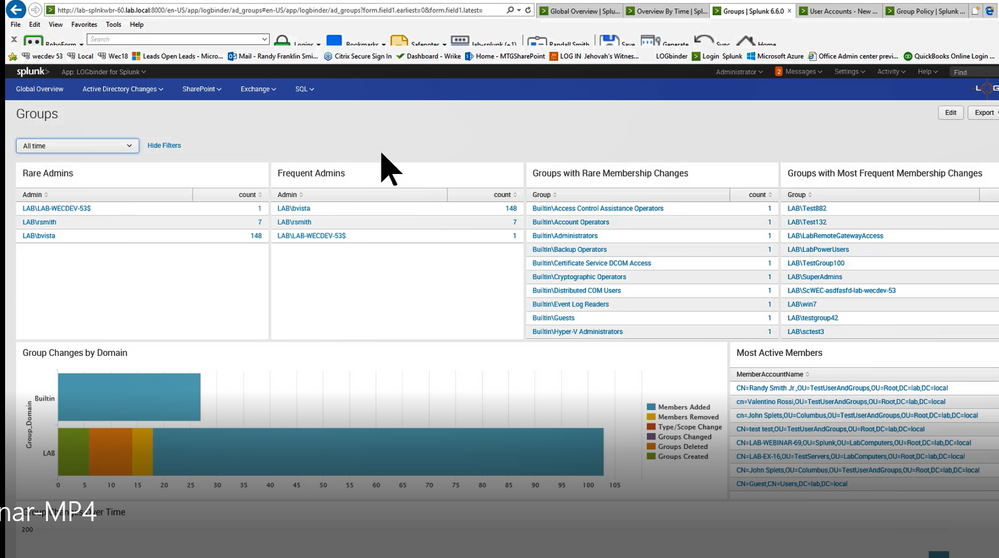
I see it now thanks. i removed the ' from 'select_winseclog_events' (EventCode=4726 OR EventCode=4768). But still no result found although these events are present in the index=main logs. Kindly help on finding how to reflect this logs on the ADChanges like the last image from splunk webinar.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Then go back to your search and replace the backticks around the macro name. It should work now.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
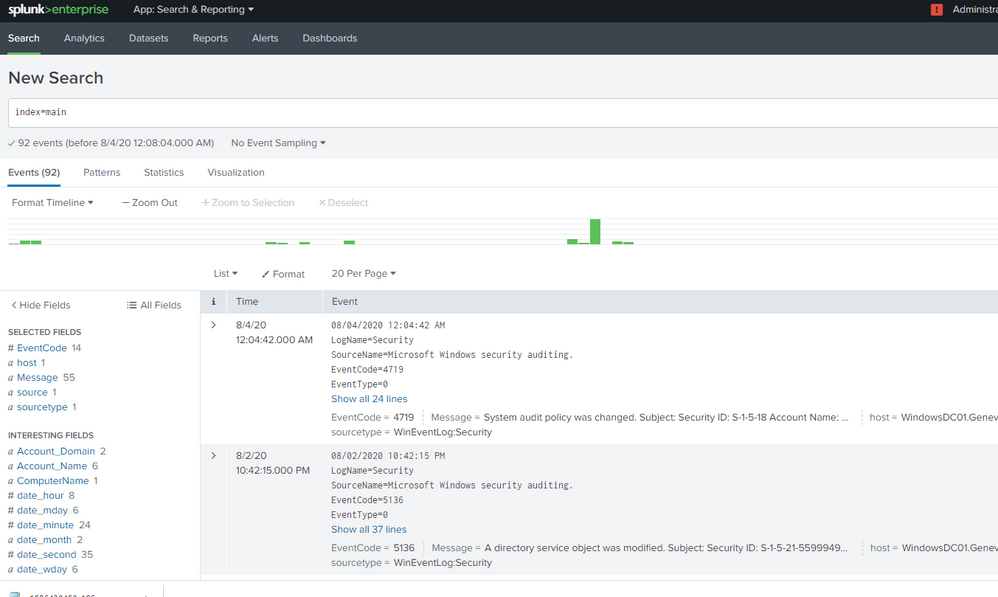
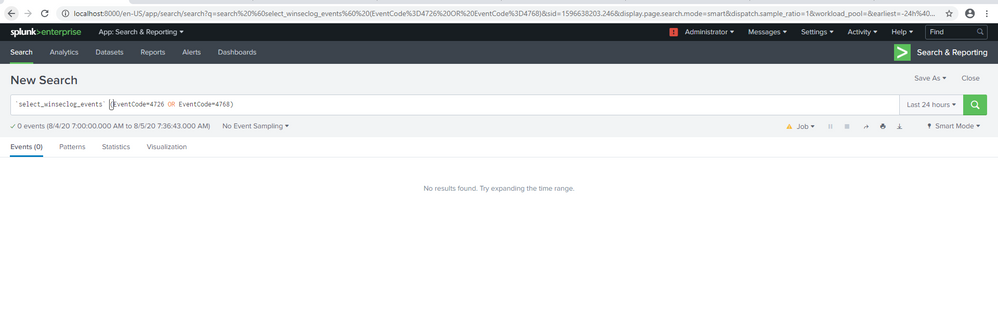
Thank you that worked. But still no result and did not reflect in the dashboard.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Now you have a different problem to solve. 🙂
A dashboard showing no results could mean there are events which mean the criteria or it could mean the search is not valid (wrong index, etc.).
Click in the search bar and type CTRL-Shift-E to expand all macros. Verify the expansion makes sense in your Splunk environment. Make changes as necessary. Run that search in a new window so see f you get results. If so, update the dashboard with the corrected search.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
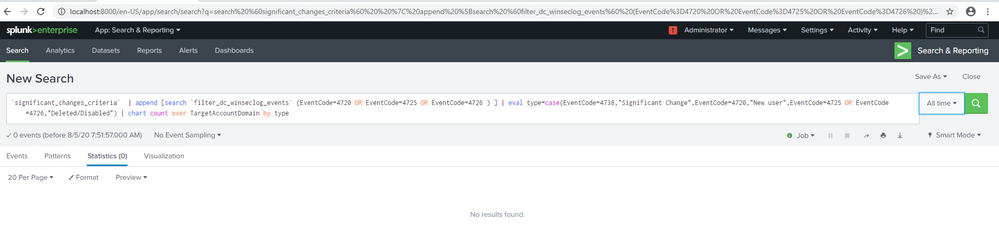
This one is for account changes by Domain. I ran it in search bar but still no result. Sorry I'm a newbie so I am not sure if those macros are correct. But even simple search like `select_winseclog_events` (EventCode=4726 OR EventCode=4768) and | inputlookup domain_controllers.. is not showing anything..
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The basic process for debugging a query is to start with the text before the first pipe and run it by itself to verify the results are expected. Add one pipe at a time until the query breaks. Then you know where to focus your efforts.
Subsearches should be run by themselves. Add | format on the end (if not already present) to see what the subsearch will pass to the main search.
I suspect the inputlookup subsearches need | format added to them.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello, Rich.
I think it is solved now. Changed select_winseclog_events definition to index=main. Thank you for your support.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Now I don't have any errors in searching but still no result. Kindly assist please. Thank you.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The solution is at the top of this thread. If your problem is similar, but the solution doesn't work for you then please post a new question.
If this reply helps you, Karma would be appreciated.