- Find Answers
- :
- Splunk Platform
- :
- Splunk Enterprise
- :
- Configure CRC salt
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I want to configure CRC Salt but I am quite not sure how write it on inputs.conf.
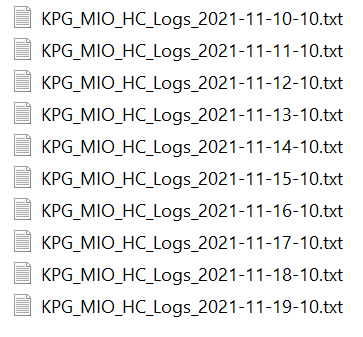
The directory on splunk is like this: /home/csaops/csasec/NFV/KPG_MIO_HC_Logs_2021-11-10-10.txt
How do I configure this configuration?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Azwaliyana,
crcSal is useful to read again a file that with a normal input configuration was already read.
As you can read at https://docs.splunk.com/Documentation/Splunk/8.2.3/Admin/Inputsconf#MONITOR:
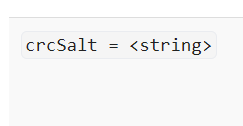
crcSalt = <string>
* Use this setting to force the input to consume files that have matching CRCs
(cyclic redundancy checks).
* By default, the input only performs CRC checks against the first 256
bytes of a file. This behavior prevents the input from indexing the same
file twice, even though you might have renamed it, as with rolling log
files, for example. Because the CRC is based on only the first
few lines of the file, it is possible for legitimately different files
to have matching CRCs, particularly if they have identical headers.
* If set, <string> is added to the CRC.
* If set to the literal string "<SOURCE>" (including the angle brackets), the
full directory path to the source file is added to the CRC. This ensures
that each file being monitored has a unique CRC. When 'crcSalt' is invoked,
it is usually set to <SOURCE>.
* Be cautious about using this setting with rolling log files; it could lead
to the log file being re-indexed after it has rolled.
* In many situations, 'initCrcLength' can be used to achieve the same goals.
* Default: empty string
you have to use
crcSal = <SOURCE>
to add also the complete file path name to the check.
Note that you have to insert in your inputs.conf the full option as you can see, it isn't to configure.
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Azwaliyana,
crcSal is useful to read again a file that with a normal input configuration was already read.
As you can read at https://docs.splunk.com/Documentation/Splunk/8.2.3/Admin/Inputsconf#MONITOR:
crcSalt = <string>
* Use this setting to force the input to consume files that have matching CRCs
(cyclic redundancy checks).
* By default, the input only performs CRC checks against the first 256
bytes of a file. This behavior prevents the input from indexing the same
file twice, even though you might have renamed it, as with rolling log
files, for example. Because the CRC is based on only the first
few lines of the file, it is possible for legitimately different files
to have matching CRCs, particularly if they have identical headers.
* If set, <string> is added to the CRC.
* If set to the literal string "<SOURCE>" (including the angle brackets), the
full directory path to the source file is added to the CRC. This ensures
that each file being monitored has a unique CRC. When 'crcSalt' is invoked,
it is usually set to <SOURCE>.
* Be cautious about using this setting with rolling log files; it could lead
to the log file being re-indexed after it has rolled.
* In many situations, 'initCrcLength' can be used to achieve the same goals.
* Default: empty string
you have to use
crcSal = <SOURCE>
to add also the complete file path name to the check.
Note that you have to insert in your inputs.conf the full option as you can see, it isn't to configure.
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Azwaliyana,
good for you, see next time!
ciao and happy splunking.
Giuseppe
P.s.: karma Points are appreciated 😉