Are you a member of the Splunk Community?
- Find Answers
- :
- Premium Solutions
- :
- Splunk Enterprise Security
- :
- How to generate an event when a risk score above 1...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So basically I'm trying to generate an event when a risk score above 100 is generated, I've come up with the below search string. Please, can you help me in identifying if anything needs to be changed?
| tstats allow_old_summaries=`allow_old_summaries_bool` sum(All_Risk.src) as src,from datamodel=Risk by All_Risk.src | where risk_score>=100 | stats values(risk_score) by src
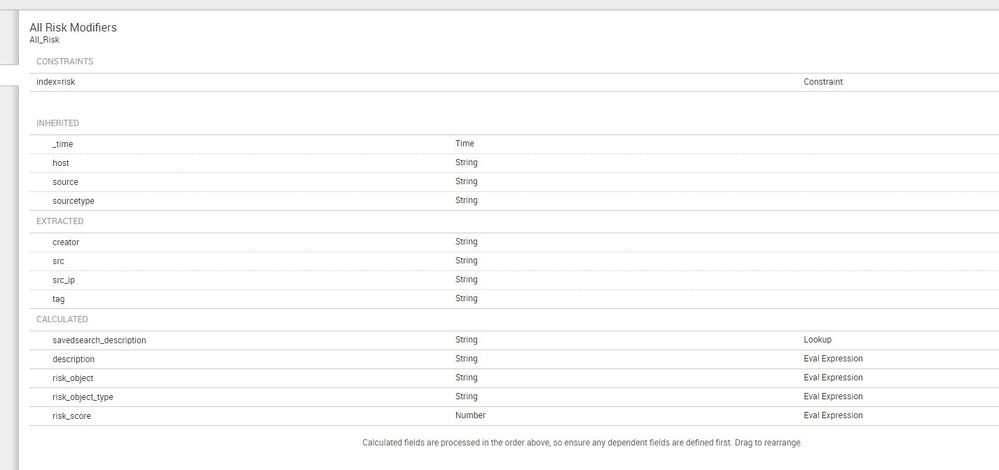
This is what my data model currently looks like.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey@emmanuelpeter,
If you are looking for events with risk_score>100 than you don't need to add stats.
Let me know if this helps!!
Thanks!!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey@emmanuelpeter,
If you are looking for events with risk_score>100 than you don't need to add stats.
Let me know if this helps!!
Thanks!!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks Deepashri.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey @emmanuelpeter,
I've converted @depashri_123's comment to an answer. If this has resolved your issue, please close the question by clicking on "Accept" button. This will help other Splunkers who might be having similar issues to know this works.