Join the Conversation
- Find Answers
- :
- Splunk Platform
- :
- Splunk Cloud Platform
- :
- Re: Priority precedence fields by sourcetype
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Priority precedence fields by sourcetype
Hi team,
I am working with Splunk Cloud "Classic" experience, and I installed one official app with different configurations. In my case, my focus is with props.conf in the stanza "sourcetype" where this props.conf creates a field called "action". I need to change this field "action" without modifying the official app, so, I created a new custom app with new props and stanza sourcetype with field "action" adding other characteristics.
After that, splunk cloud continues applying the old configuration from the official app and it didn't take the new attributes.
Note: I am using default folder in each apps for locate the props file because Splunk Cloud doesn't allow using local folder
Someone know, how can I do that?
priority precedence fields by sourcetype
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I just stumbled on this and thought I'd add a few other notes on this...
with props.conf in the stanza "sourcetype" where this props.conf creates a field called "action".
Just to confirm, how is the field being created? I'm assuming you mean a search time field as opposed to an index time field. Skimming the #Mimecast for Splunk app it looks like there are field aliases, and eval statements for different source types around the `action` field which are both search time... but I could be missing something. If you were instead referring to an index time transformation, not only is precedence order different, but also reingestion of data would need to happen before things take effect.
Speaking of precedence order, probably time to mention that search time attributes use user / app precedence order as documented: https://docs.splunk.com/Documentation/Splunk/latest/Admin/Wheretofindtheconfigurationfiles#Precedenc...
Some effects of this is 1) your app needs to be lexographically after the app you're trying to override (precedence by name of other apps is reverse lexographic order as opposed to forward lexographic order)
2) your app needs to export the corresponding settings 3) even with all that done, your settings from other apps will lose if searches are being launched from within the mimecast app because the current app's settings gets highest precedence for the same stanza. (may or may not be an issue, I'm not familiar enough with the app to say, but it is a potential edge case).
Here's where we need to address something else:
Splunk Cloud doesn't allow using local folder
Splunk Cloud doesn't let you upload an app with a local folder, however, Calculated fields, and field aliases are both editable via the UI, so you could actually create a local override within the context of the original TA itself via the UI and those would win. (since merging between default and local per app happens first with user/app context resolution order). No additional app needed necessarily (that gets into a long term management discussion).
@richgalloway already provided an alternative solution since within props.conf, there is an additional merging between stanzas for sourcetypes, hosts, and sources... But if course need to be careful with those since you could affect other sourcetypes too.
From the props.conf.spec:
**[<spec>] stanza precedence:**
For settings that are specified in multiple categories of matching [<spec>]
stanzas, [host::<host>] settings override [<sourcetype>] settings.
Additionally, [source::<source>] settings override both [host::<host>]
and [<sourcetype>] settings.
In either case once settings are in place on the search head, they need to be replicated to your indexers as part of the knowledge bundle before they can take effect during a search... So if you're already over the 3GB limit there need to spend some time trimming the bundle size.
Seeing resolved search time precedence can be done per stanza with the properties rest endpoint on the search head, and/or the btool command. (make sure to specify the appropriate `--app` and `--user` context for correct resolution order of search time values).
(And before you say but btool is an enterprise only command.. I may have brought it to Cloud as a SPL command along with a knowledge bundle utility in Admins Little Helper for Splunk ... my officially unsupported but I think its useful side project Check it out on Splunkbase: https://splunkbase.splunk.com/app/6368 </shameless plug> )
Hope these notes help you and others in the future.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
When two apps set define values for the same sourcetype, the apps are applied in lexicographical order. If you want your app to have precedence, give it a name that comes before the official app.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Both
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
it doesn't work to me, i am using de ofial app Mimecast for Splunk, and i created two custom apps called Mimecast for LiveSOC and Mimecast for neither works
what name do you recommend to me using for that?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please elaborate on "it doesn't work". What results are you expecting and what do you get?
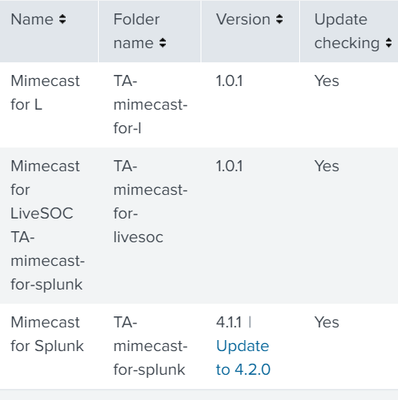
What is that screenshot intended to show? I see the name for the second app was mis-entered in app.conf and that both of the first two apps should have check_for_updates=false. It's not clear how the screenshot demonstrates anything not working.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
HI
The screenshot was an example
I installed ofcial app "Mimecast for Splunk" and app folder "TA-mimecast-for-splunk", and I created a custom app called "Mimecast for LiveSOC" and the folder app "TA-mimecast-for-livesoc" , I need to know if the custom app name is correct for force the data to use the configuration from "sourcetype" from custom app and not the oficial app
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The custom app will need a different sourcetype name if the sourcetype is to have different settings from the official app. That means you also will need to change the input to use the custom sourcetype.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi
The client needs to use the same sourcetype, they don't want to change anything from official app, cuz the inputs don't allow to change sourcetype in the configuration, the inputs used are from official app and these assign sourcetype automatically
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If the sourcetype cannot be changed then the custom app should specify its props using source:: or host::.
If this reply helps you, Karma would be appreciated.